Managing Isolated Files
HSS can isolate detected threat files. Files that have been isolated are displayed on a slide-out panel on the Events page and cannot harm your servers. You can click Isolated Files on the upper right corner to check them, You can isolate files or recover them.
The following types of alarm events support online isolation and killing:
- Malicious program (cloud scan)
- Abnormal process behavior
Isolating and Killing Files
- Log in to the management console.
- In the upper left corner of the page, select a region, click
 , and choose .
, and choose . - In the navigation pane, choose Intrusions > Events.
Figure 1 Events page
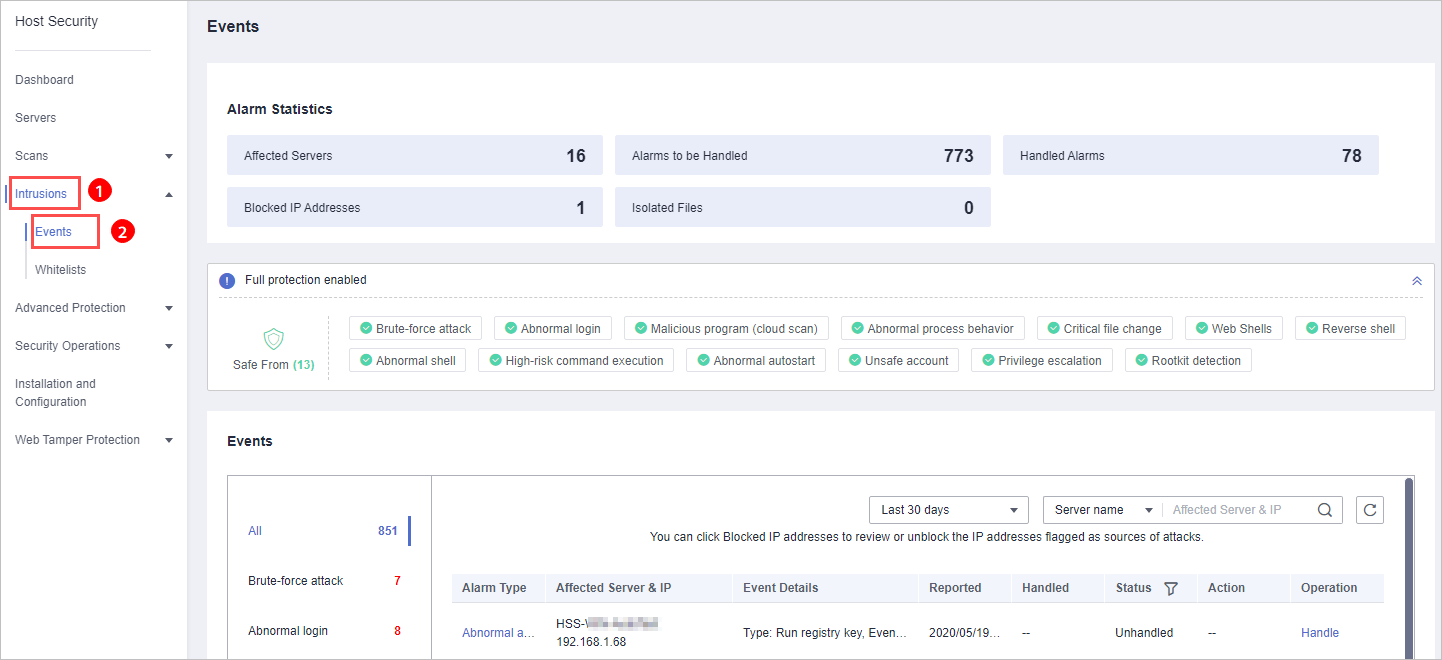
- Select an event of the Malicious program (cloud scan) or Abnormal process behavior type, and click Handle. In the dialog box that is displayed, click Isolate and Kill.
Figure 2 Isolating and killing malicious programs
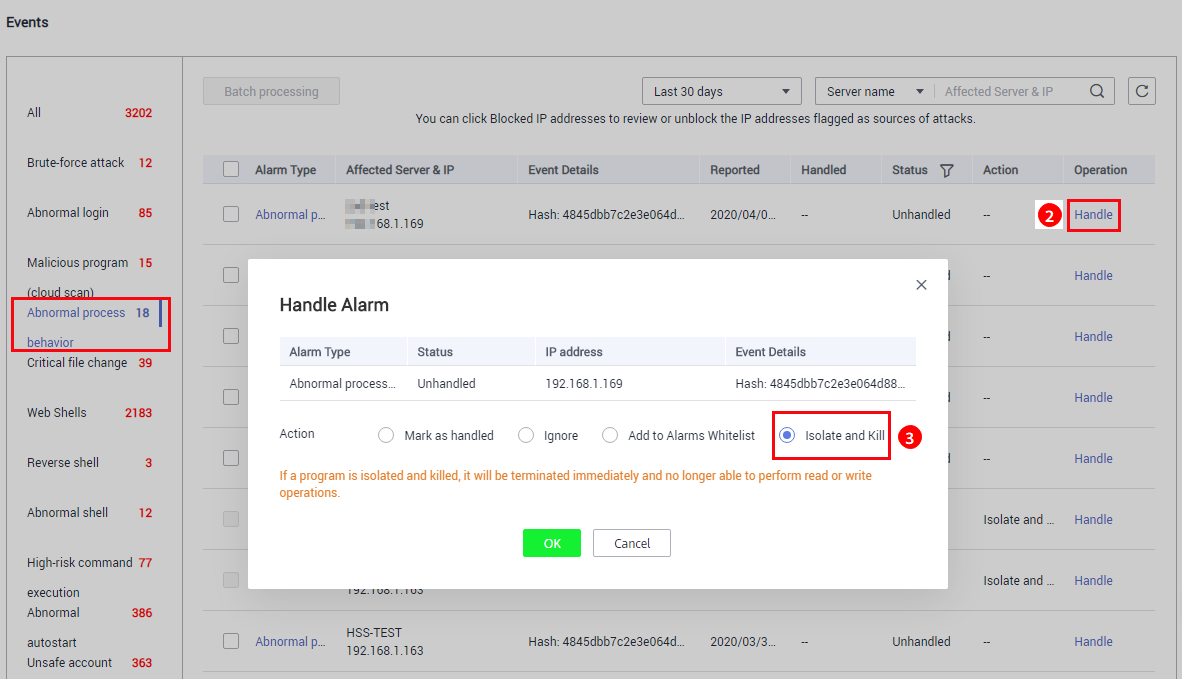
- Click OK. Files that have been isolated are displayed on a slide-out panel on the Events page and cannot harm your servers. You can click Isolated Files on the upper right corner to check them.
Checking Isolated Files
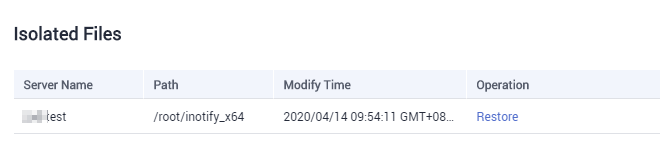
- On the Events page, click Isolated Files on the upper right corner.
- Check the servers, names, paths, and modification time of the isolated files, as shown in Figure 3.
Figure 3 Checking isolated files
Recovering Isolated Files
- Click Restore in the Operation column of an isolated file.
- Click OK.Note
Recovered files will no longer be isolated. Exercise caution when performing this operation.
Parent topic: Intrusion Detection
- Isolating and Killing Files
- Checking Isolated Files
- Recovering Isolated Files