Checking and Handling Protection Events
If a ransomware protection policy takes effect on servers, HSS will check operations performed on monitored files on the servers, mark the operations as trusted or untrusted, and report alarms on operations performed by the applications that are untrusted or not specified in the policy.
The event management page displays untrusted operations that match a policy and operations performed by that applications that are not specified in any policies.
You are advised to pay attention to these events and handle them in a timely manner.
Checking Ransomware Prevention Events
- Log in to the management console.
- In the upper left corner of the page, select a region, click
 , and choose .
, and choose . - On the Ransomware page, click the Events tab, as shown in Figure 1.
Figure 1 Ransomware prevention events
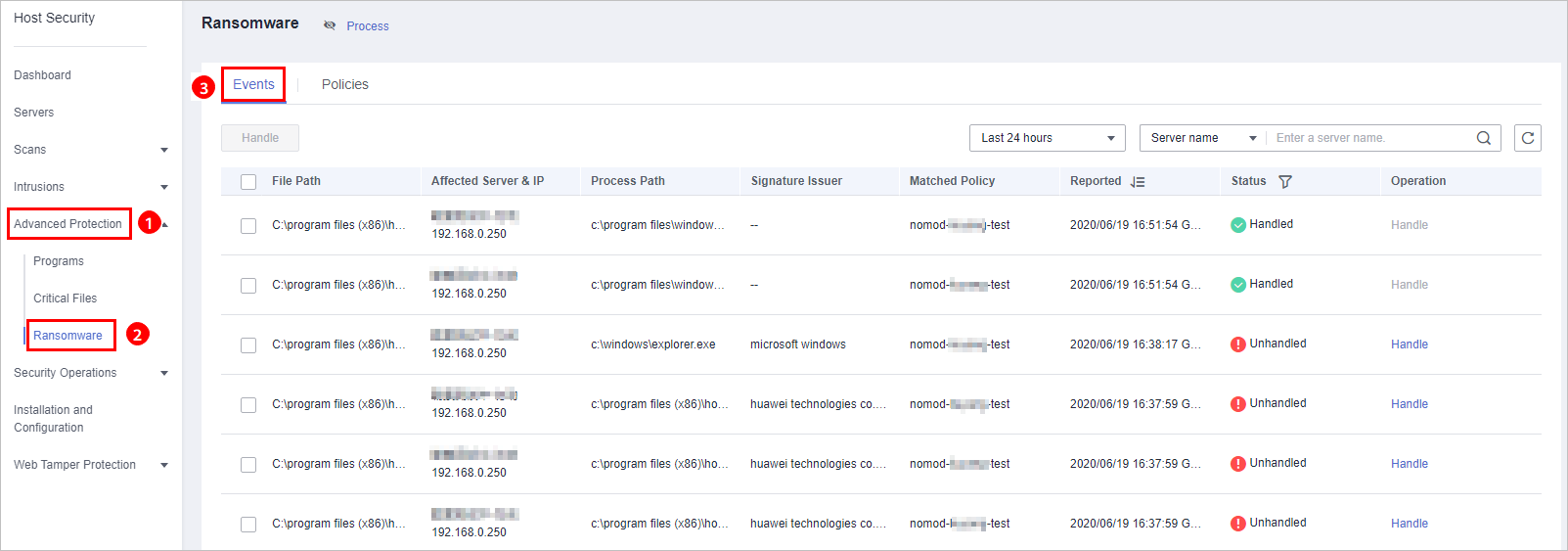
Table 1 Ransomware prevention event parameters Parameter
Description
File Path
Path of the file operated by an application
Affected Server & IP
Name and IP address of the server where the file operation is performed
Process Path
Path of the Application that performs operations on files
Signature Issuer
Signature issuer
Matched Policy
Policy that matches the alarm
Reported
Time when an alarm is reported
Status
Event status. Its value can be Handled or Unhandled.
Handling Ransomware Prevention Events
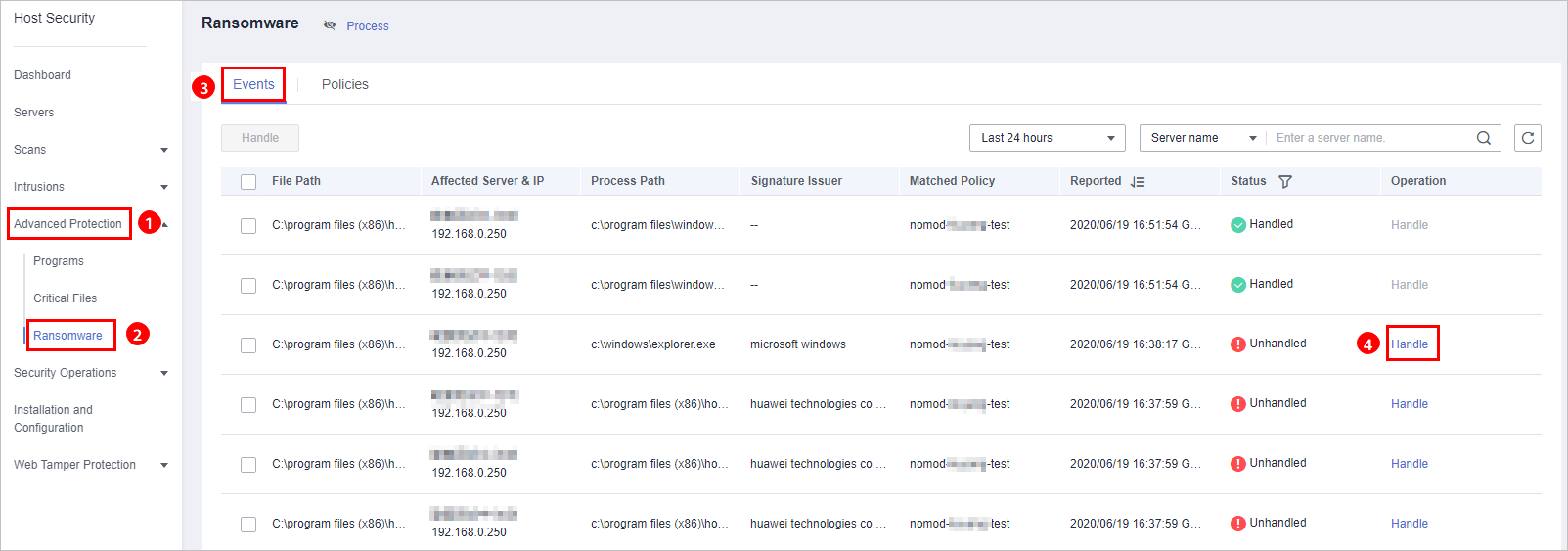
- In the Operation column of an event, click Handle, as shown in Figure 2.
Figure 2 Checking ransomware prevention events
- In the displayed dialog box, select Trusted or Untrusted, as shown in Figure 3.
Figure 3 Handling ransomware events
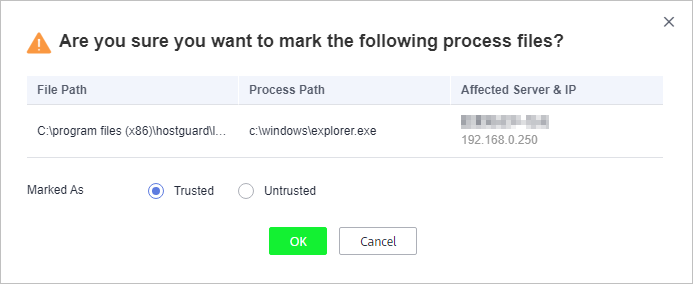
Table 2 Event handling parameters Marked As
Description
Trusted
An application marked as trusted will not trigger alarms if it performs operation on files under monitored paths.
Untrusted
An application marked as untrusted will trigger alarms if it performs operation on files under monitored paths.
- Click OK.
- Checking Ransomware Prevention Events
- Handling Ransomware Prevention Events