Creating a Protection Policy
To protect your servers from ransomware, you can create a policy, set critical file paths in the policy, and enable machine learning.
Machine learning automatically collects and aggregates normal application behavior on the servers associated with the policy. Operations on files performed by untrusted applications or applications that are not specified in the policy will trigger alarms.
Creating a Protection Policy
- Log in to the management console.
- In the upper left corner of the page, select a region, click
 , and choose .
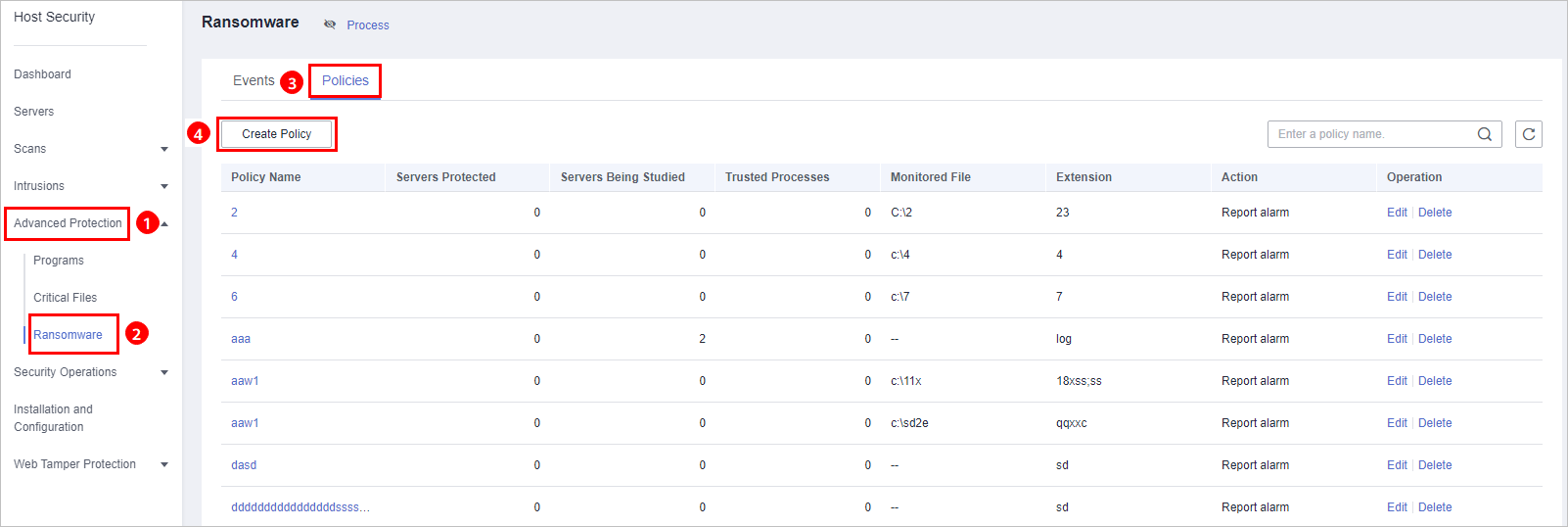
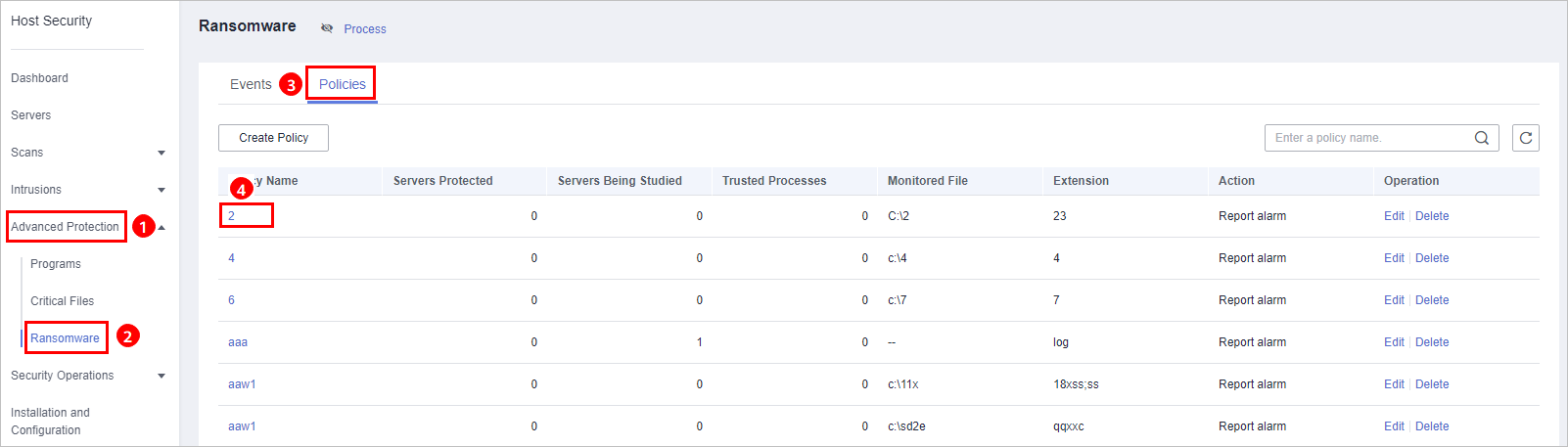
, and choose . - On the Ransomware page, click the Policies tab, and click Create Policy, as shown in Figure 1.
Figure 1 Policy management
- Set policy details, as shown in Figure 2.
Figure 2 Configuring a ransomware prevention policy
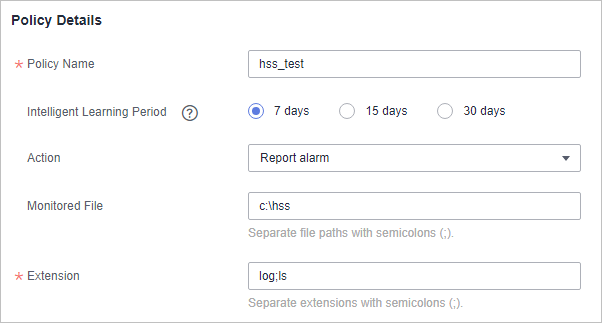
Table 1 Basic information parameters Parameter
Description
Policy Name
Ransomware prevention policy name
Intelligent Learning Period
Select 7 days, 15 days, or 30 days.
HSS uses a machine learning engine to identify if an application has possibly tampered with any of the files on your servers.
Action
Action taken when suspicious operations on monitored files are detected. For example, report alarms.
Monitored File
Path of monitored files. Multiple paths are separated by semicolons (;). Operations on the files in these paths are monitored.
If no paths are specified, all the files on the servers associated to the policy are monitored.
Extension
Extension of monitored files. Multiple paths are separated by semicolons (;).
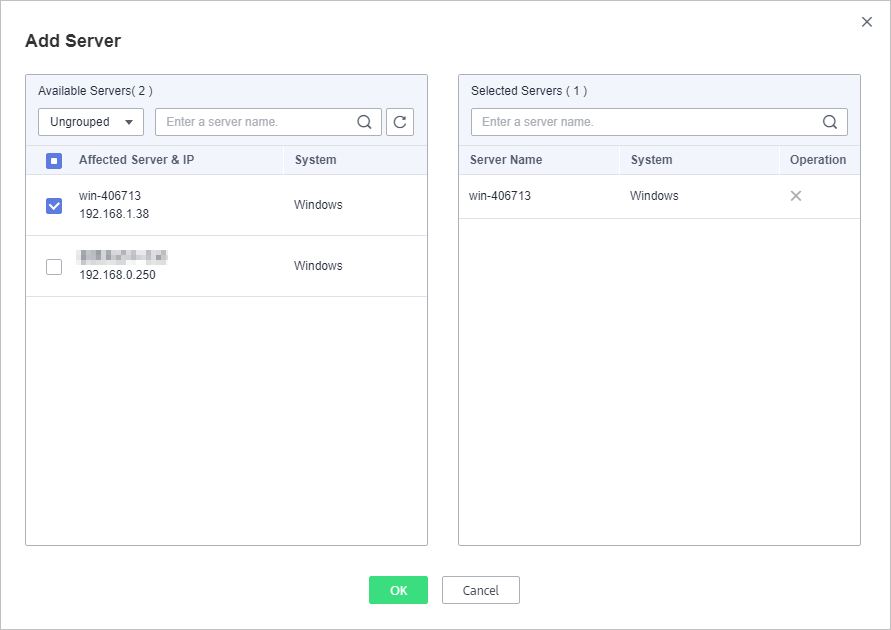
- Click Add Server. In the displayed Add Server dialog box, select associated servers, as shown in Figure 3.
Figure 3 Associating servers
- Click OK.Note
- You can check the name, IP address, and system of the associated server.
- To remove an associated server, click Delete in the Operation column.
- Click Create and Learn.
Created policies will be displayed in the policy list, as shown in Figure 4.
Figure 4 Ransomware prevention policy list
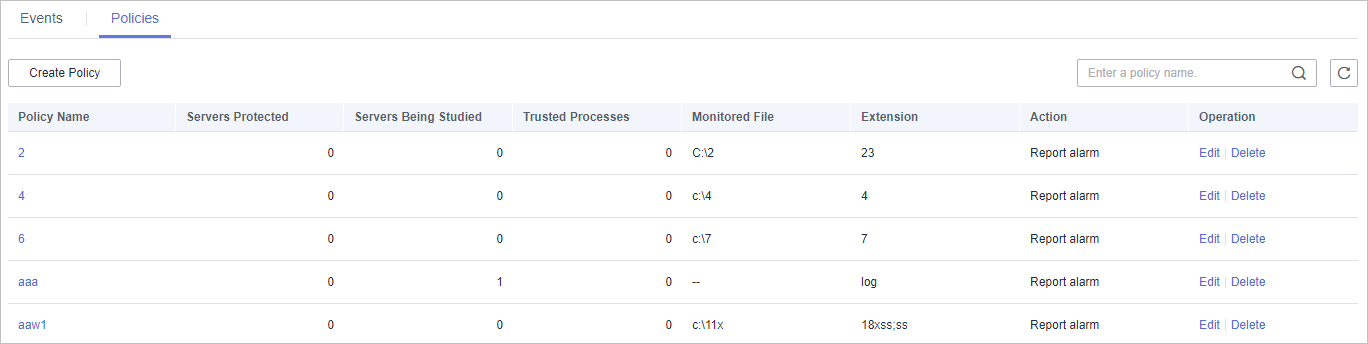
Table 2 Policy list parameters Parameter
Description
Policy Name
Intelligent learning policy name
Servers Protected
Number of servers protected by the policy
Servers Being Studied
Number of servers where the learning is performed
Trusted Processes
Number of trusted processes. After the intelligent learning policy takes effect, HSS automatically identifies and counts trusted processes on your server.
Monitored File
Path of monitored files. Multiple paths are separated by semicolons (;). Operations on the files in these paths are monitored.
If no paths are specified, all the files on the servers associated to the policy are monitored.
Extension
Extension of monitored files. Multiple paths are separated by semicolons (;).
Action
Action taken when suspicious operations on monitored files are detected.
For example, report alarms.
Associating Servers
You can associated servers to an existing intelligent learning policy on the Associated Servers tab on the policy details page.
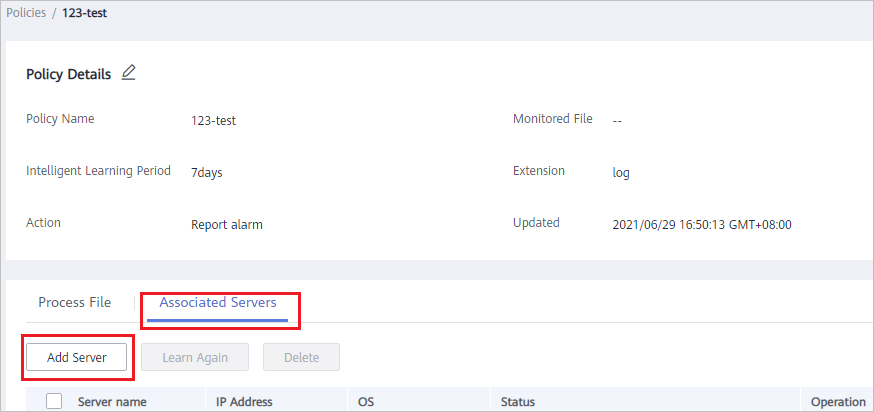
- Click the name of a policy. The policy details page is displayed, as shown in Figure 5.
Figure 5 Accessing the policy details page
- Click the Associated Servers tab and click Add Server, as shown in Figure 6.
Figure 6 Adding associated servers
- In the displayed Add Server dialog box, select servers, as shown in Figure 7.
Figure 7 Associating servers

- Click OK.
After associated servers are added, you can check their server names, IP addresses, systems, and policy. By default, the initial policy status is Learning.
After the learning is complete, the policy status changes to Learning complete. Policy in effect. The ransomware prevention policy will automatically take effect on all servers associated with it.
Follow-Up Procedure
Editing a policy
You can click Edit to modify the policy name, intelligent learning period, protection status, monitored file paths, and file extensions.
Deleting a policy
You can click the Delete button to delete a policy. Servers associated with it will no longer be protected.
- Creating a Protection Policy
- Associating Servers
- Follow-Up Procedure