Suggestions on Fixing Unsafe Settings
This topic provides suggestions on how to fix unsafe settings found by HSS.
Modifying the Password Complexity Policy
- To monitor the password complexity policy on a Linux server, install the Pluggable Authentication Modules (PAM) on the server. For details, see How Do I Install a PAM in a Linux OS?
- For details about how to modify the password complexity policy on a Linux server, see How Do I Install a PAM and Set a Proper Password Complexity Policy in a Linux OS?
- For details about how to modify the password complexity policy on a Windows server, see How Do I Set a Secure Password Complexity Policy in a Windows OS?
After modifying the password complexity policy, you are advised to perform manual detection immediately to verify the result. If you do not perform manual verification, HSS will automatically check the settings the next day in the early morning.
Weak Passwords
- To enhance server security, you are advised to modify the accounts with weak passwords for logging in to the system in a timely manner, such as SSH accounts.
- To protect internal data of your server, you are advised to modify software accounts that use weak passwords, such as MySQL accounts and FTP accounts.
After modifying weak passwords, you are advised to perform manual detection immediately to verify the result. If you do not perform manual verification, HSS will automatically check the settings the next day in the early morning.
Unsafe Configurations
Insecure configurations of key applications will probably be exploited by hackers to intrude servers. Such configurations include insecure encryption algorithms used by SSH and Tomcat startup with root permissions.
HSS can detect unsafe configurations provide detailed suggestions. You can check, fix, or ignore a risky item.
- Modifying unsafe configuration items
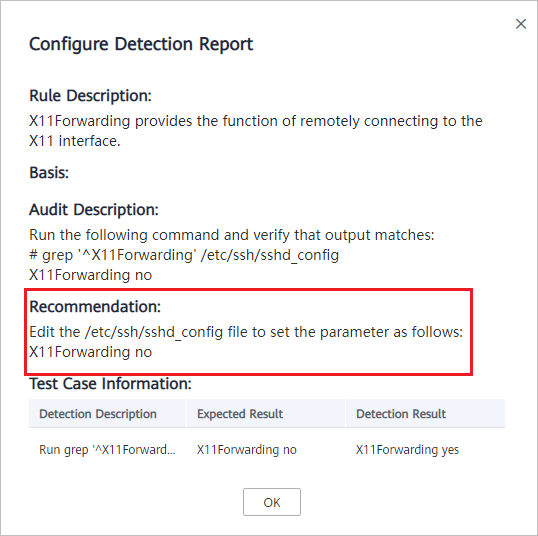
You can confirm the detection result based on details under Audit Description and fix settings as instructed in Recommendation.
You are advised to fix the configurations with high severity immediately and repair those with medium or low severity based on service requirements.
Figure 1 Detection report
- Ignoring trusted configuration items
Select a detection rule and click Ignore in the Operation column to ignore it. To ignore multiple detection rules, select them and click the Ignore button above the list to batch ignore them.
To unignore an ignored detection rule, click Unignore in the Operation column. To unignore multiple ignored detection rules, select rules and click Unignore in the upper left corner above the detection rule list.
After modifying configuration items, you are advised to perform manual detection immediately to verify the result. If you do not perform manual verification, HSS will automatically check the settings the next day in the early morning.
- Modifying the Password Complexity Policy
- Weak Passwords
- Unsafe Configurations