Checking for Unsafe Settings
HSS checks your software for weak password complexity policies and other unsafe settings, and provides suggestions for fixing detected risks.
Check Interval
- HSS automatically performs a comprehensive check in the early morning every day.
- To manually start a scan, click Manual Detection in the upper right corner of the Servers page.
HSS will scan your servers for software information, Linux software vulnerabilities, Windows system vulnerabilities, Web-CMS vulnerabilities, web shells, password risks, and unsafe settings configuration.
All these items are concurrently checked and the total scan duration is less than 30 minutes.
- To view the scan details of a server, click its scan result in the Detection Result column on the Servers and Quotas page.
You can also scan for password risks or unsafe configurations alone. On the Unsafe Settings tab of the result page, click the Password Risks or Unsafe Configurations subtab and click Manual Detection. The scan takes less than 30 minutes.
Alarm Policies
HSS checks your servers for weak passwords and unsafe software settings, and generates alarms if it finds any of them.
You can enable alarm notifications on the Installation and Configuration page of the HSS console. For details, see Enabling Alarm Notification for the Basic/Enterprise/Premium Edition.
Check Items
Item | Description |
|---|---|
Password complexity policies | Password complexity policies on system accounts |
Common weak passwords | Weak passwords defined in the common weak password library Common weak passwords of MySQL, FTP, and system accounts |
Unsafe configurations | Unsafe configurations in Tomcat, SSH, Nginx, Redis, Apache2, and MySQL5 |
Procedure
- Log in to the management console.
- In the upper left corner of the page, select a region, click
 , and choose .
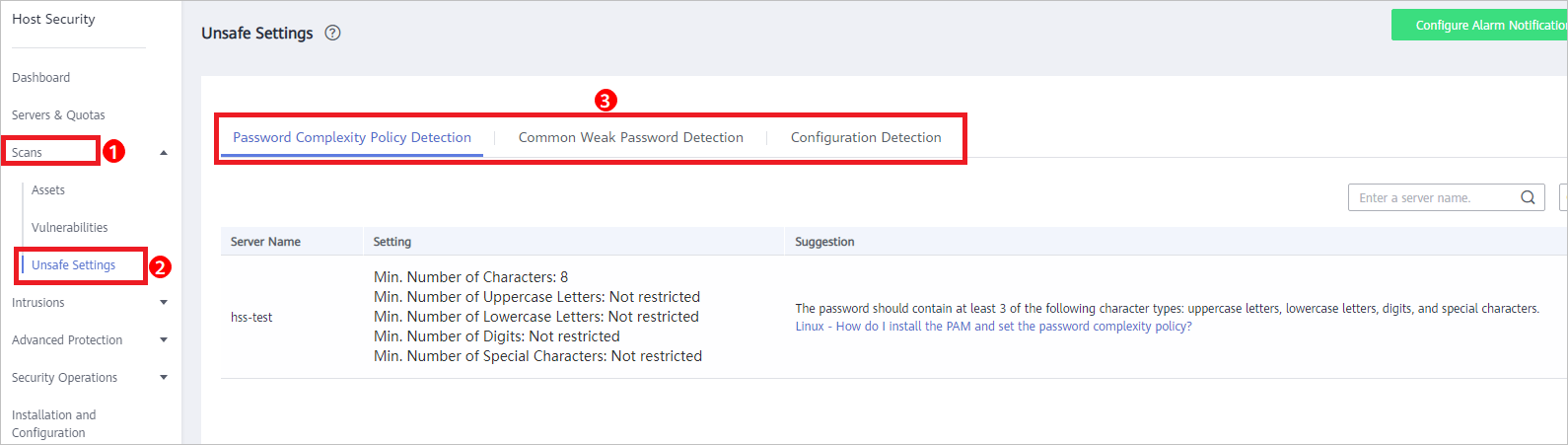
, and choose . - Choose Scans > Unsafe Settings and check detected unsafe settings.
Figure 1 Unsafe settings
Exporting a Check Report
On the upper right corner of the table on the Configuration Detection tab, click  to download reports.
to download reports.
The detection result of a single server cannot be separately exported.
- Check Interval
- Alarm Policies
- Check Items
- Procedure
- Exporting a Check Report