Adding a Monitored File
File integrity monitoring (FIM) checks the files in your OSs, applications, and other components for tampering, helping you meet PCI-DSS requirements.
FIM compares files with their versions in the previous scan to check whether files have been modified, and whether the modifications are suspicious.
FIM checks the integrity of Linux files and manages operations on them, including:
- Create and delete files
- Modify files (changes in file size, ACLs, and content hashes)
The registry monitoring function will be available soon.
You are advised to monitor only the files that are important for systems and applications, and are rarely modified.
If you monitor files that are frequently modified, by applications or OSs, such as log files and text files, a lot of false alarms will be generated.
Enabling FIM
- Log in to the management console.
- In the upper left corner of the page, select a region, click
 , and choose .
, and choose . - On the Critical Files page, click
 to enable FIM, as shown in Figure 1. The default setting is
to enable FIM, as shown in Figure 1. The default setting is  .
.Figure 1 Enabling FIM
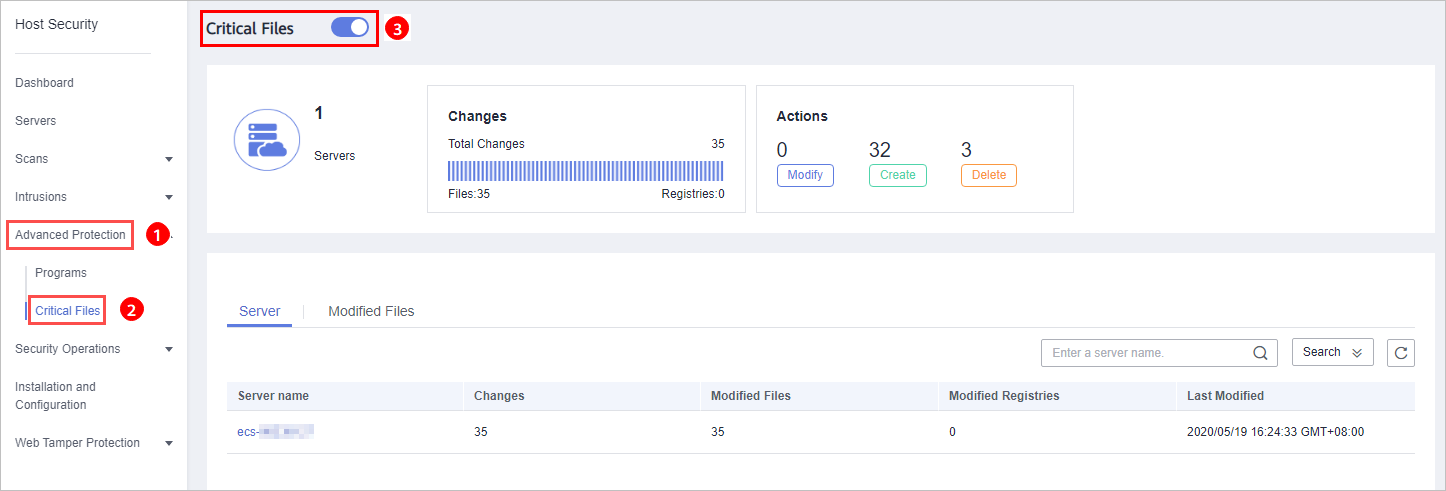
- Check the total number of servers, number of modified files, types of modifications, risks, affected servers, and modified files.
Adding a Monitored File
To add a management file, ensure that:
- You have deployed the Integrity check on critical files policy on servers.
- The Integrity check on critical files policy has been enabled.
Perform the following steps to add a monitored file:
- Log in to the management console.
- In the upper left corner of the page, select a region, click
 , and choose .
, and choose . - In the navigation pane, choose Security Operations > Policies.
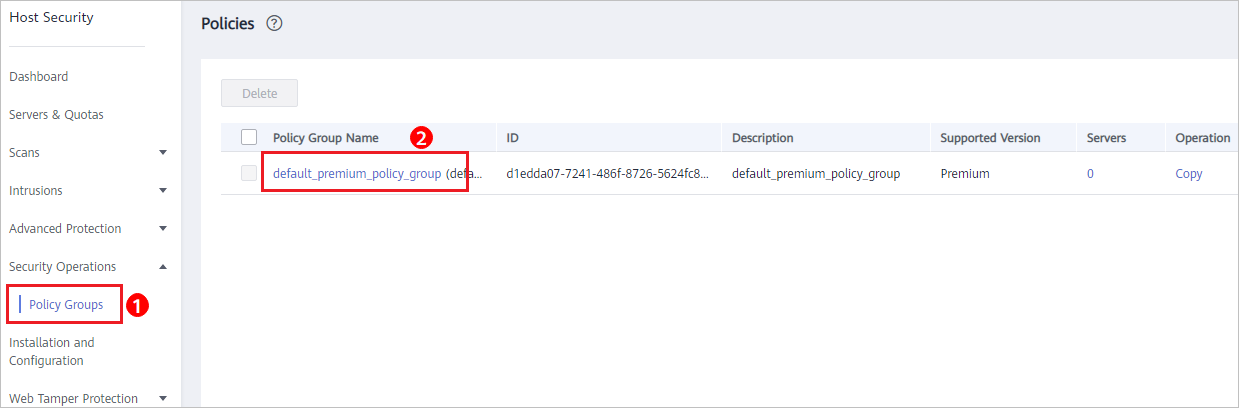
- On the Policies page, click the policy group deployed on your servers. Take the default policy group of the premium edition group as an example, as shown in Figure 2.
Figure 2 Default policy group
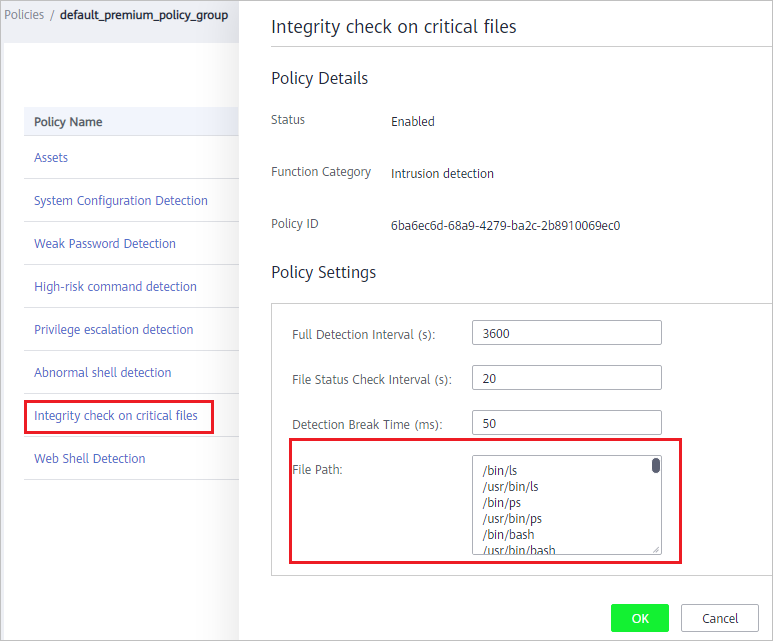
- Click Integrity check on critical files and set monitored files, as shown in Figure 3.
For details about how to configure the Integrity check on critical files policy, see File Integrity Monitoring.
Figure 3 Opening the Integrity check on critical files policy
- Click OK.
Follow-Up Procedure
Disabling FIM
To disable FIM, click  . If the function is disabled, HSS no longer monitors your files or displays FIM statistics.
. If the function is disabled, HSS no longer monitors your files or displays FIM statistics.
- Enabling FIM
- Adding a Monitored File
- Follow-Up Procedure