Viewing Details of a Vulnerability
HSS detects Linux software vulnerabilities, Windows system vulnerabilities, and Web-CMS vulnerabilities.
On the Vulnerabilities page, you can view the basic information and status about vulnerabilities and handle them based on Urgency.
In the chart of top 5 servers, only the vulnerabilities of High urgency are displayed.
Detection Mechanisms
Type | Mechanism |
|---|---|
Linux vulnerabilities | HSS detects vulnerabilities in the system and software (such as SSH, OpenSSL, Apache, and MySQL) based on vulnerability libraries, reports the results to the management console, and generates alarms. |
Windows vulnerabilities | HSS subscribes to Microsoft official updates, checks whether the patches on the server have been updated, pushes Microsoft official patches, reports the results to the management console, and generates vulnerability alarms. |
Web-CMS vulnerabilities | HSS checks web directories and files for Web-CMS vulnerabilities, reports the results to the management console, and generates vulnerability alarms. |
Vulnerabilities detected in the past 24 hours are displayed. The server name in a vulnerability notification is the name used when the vulnerability was detected, and may be different from the latest server name.
Check Interval
HSS automatically performs a comprehensive check in the early morning every day.
Fixing Linux or Windows Vulnerabilities
- Log in to the management console.
- In the upper left corner of the page, select a region, click
 , and choose .
, and choose . - Open the Linux Vulnerabilities or Windows Vulnerabilities tab.
Figure 1 Viewing Linux or Windows vulnerability scan results
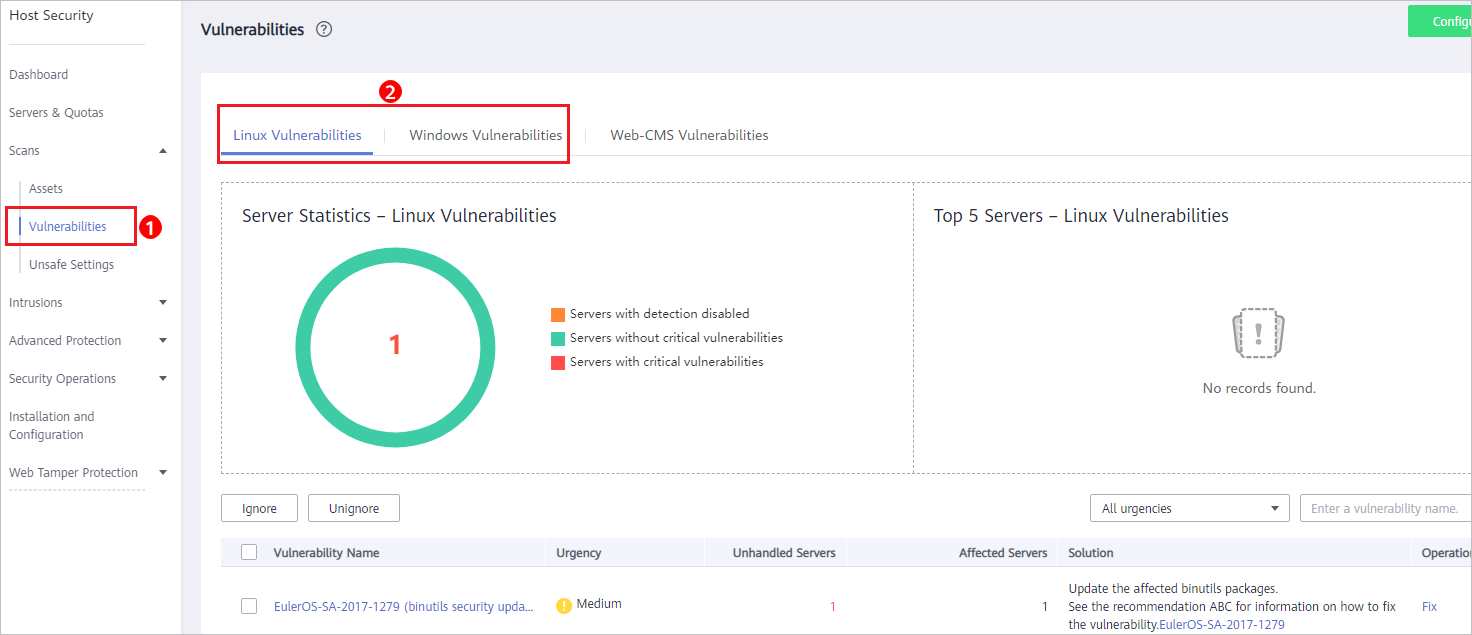
- Click a vulnerability name to view its basic information, solution, and CVE description.
Figure 2 Checking vulnerability details
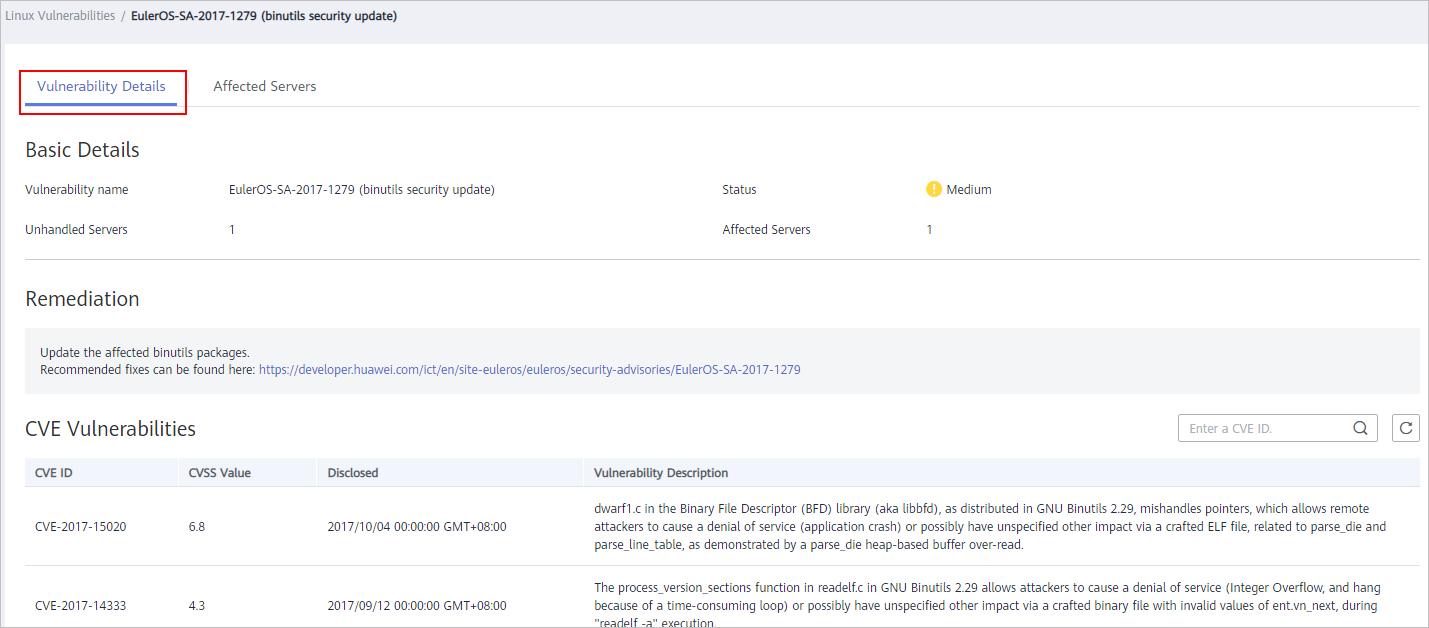
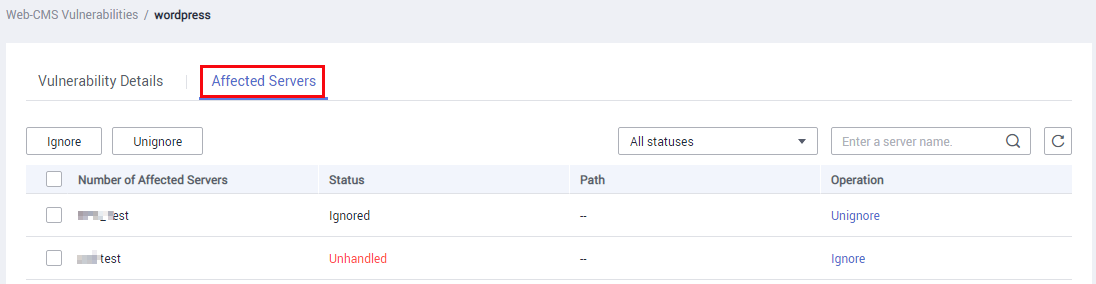
- Check the servers affected by the vulnerability.
Figure 3 Checking affected servers
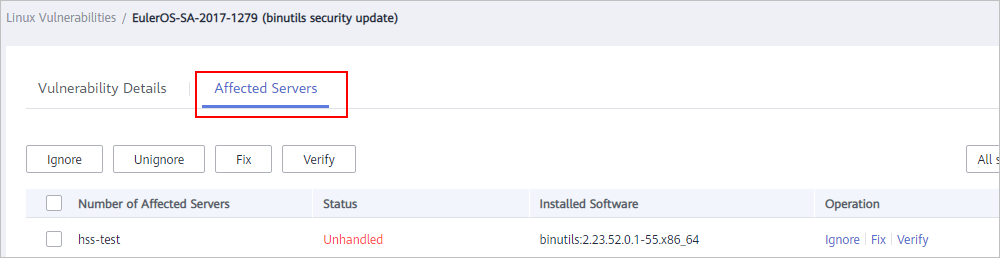
- To fix the vulnerability, click Fix.
- To ignore the vulnerability, click Ignore. HSS will no longer generate alarms for this vulnerability.
- After the vulnerability is fixed, you can click Verify to verify the fix.
HSS performs a full check every early morning. If you do not perform a manual verification, you can view the system check result on the next day after you fix the vulnerability.
If a vulnerability fails to be rectified, click View Cause to check the details.
Fixing Web-CMS Vulnerabilities
- Log in to the management console.
- In the upper left corner of the page, select a region, click
 , and choose .
, and choose . - Open the Web-CMS Vulnerabilities tab.
Figure 4 Viewing Web-CMS vulnerability detection results
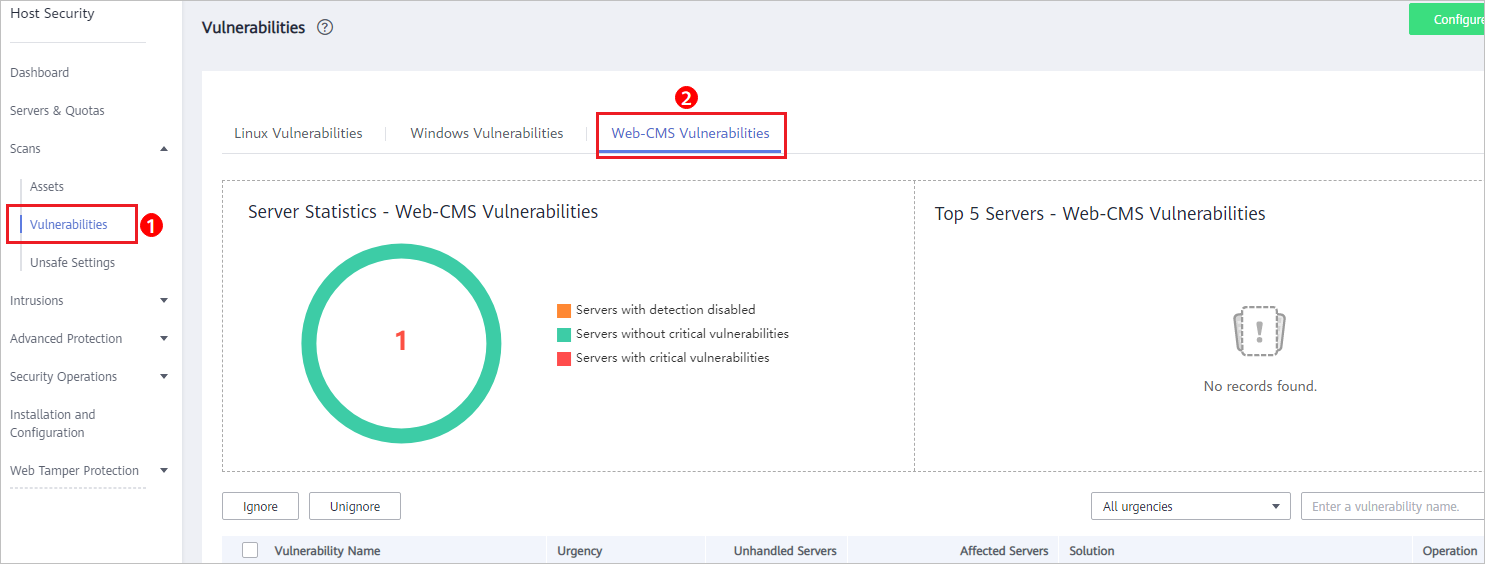
- Click the vulnerability name to view its details and affected servers.
- No Fix options are provided in the Operation column. You need to manually fix the vulnerabilities based on the suggestions provided.
- After the vulnerability is fixed, manually verify the result. HSS performs a full check every early morning. If you do not perform a manual verification, you can view the system check result on the next day after you fix the vulnerability.
- To ignore the vulnerability, click Ignore. HSS will no longer generate alarms for this vulnerability.
Figure 5 Vulnerability details
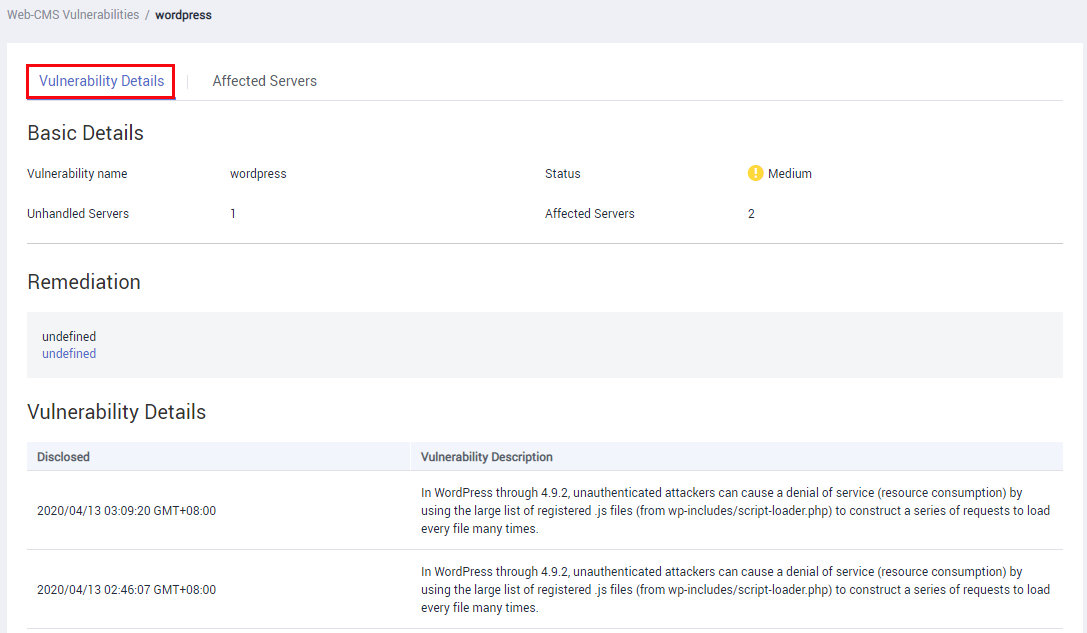
Figure 6 Affected servers
Exporting a Vulnerability Report
In the upper right corner of the vulnerability list, click  to export the vulnerability report.
to export the vulnerability report.
- Detection Mechanisms
- Check Interval
- Fixing Linux or Windows Vulnerabilities
- Fixing Web-CMS Vulnerabilities
- Exporting a Vulnerability Report