Checking the Whitelist Policy List
Application Recognition Service (ARS) scans all the applications running on your servers for uncertified or unauthorized applications, helping you maintain a secure runtime.
Function Description
Set whitelist policies, and determine whether applications are Trusted, Untrusted, or Unknown. The applications that are not whitelisted are not allowed to run. This function protects your servers from untrusted or malicious applications, reducing unnecessary resource usage.
You can create a whitelist policy and apply it to your servers. HSS will check whether suspicious or malicious processes exist on the servers, and generate alarms or isolate the processes that are not in the whitelist.
- An alarm is generated when an application not in the whitelist is started.
- An application not in the whitelist is probably a new normal application, or a malicious program implanted through intrusion.
- If the alarmed application is normal, frequently used, or a third-party application you installed, you are advised to add it to the whitelist. HSS will no longer report alarms when the application starts.
- If the application is malicious, you are advised to delete it in a timely manner and check whether your configuration files, such as scheduled task files, have been tampered with.
Checking the Whitelist Policy List
- Log in to the management console.
- In the upper left corner of the page, select a region, click
 , and choose .
, and choose . - On the Programs page, click the Whitelist Policies tab, as shown in Figure 1.
Figure 1 Checking the whitelist policy list
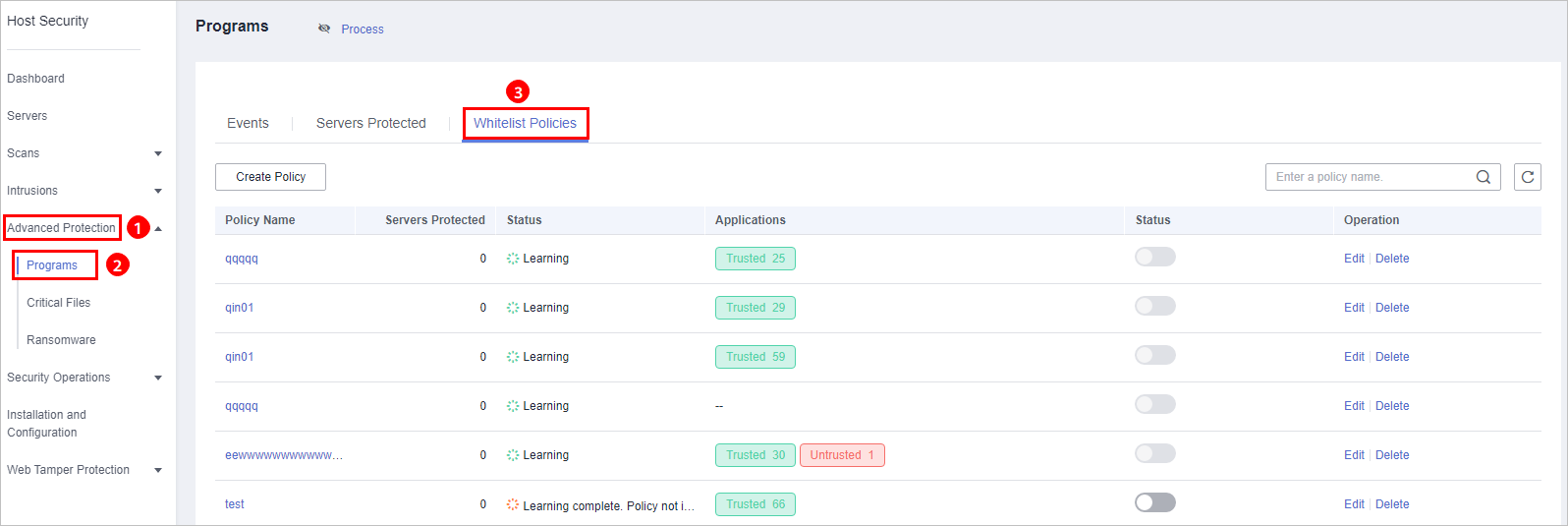
Table 1 Policy list parameters Parameter
Description
Policy Name
Whitelist policy name
Servers Protected
Number of servers where the whitelist policy takes effect
Status
Policy status. Its value can be:
- Learning
Intelligent learning is in progress.
After a policy is created, the intelligent learning function automatically analyzes operations on the servers you selected. The status of a new policy is Learning.
- Learning complete. Policy not in effect
Intelligent learning is complete. You need to manually enable the policy for it to take effect.
To enable the policy, click
 in the row where it locates. HSS will automatically check whether the application running on your servers are trustworthy, and mark them as trusted, untrusted, or unknown.
in the row where it locates. HSS will automatically check whether the application running on your servers are trustworthy, and mark them as trusted, untrusted, or unknown. - Learning complete. Policy in effect
Intelligent learning is complete. The policy has taken effect on associated servers.
Applications
Number of trusted, untrusted, and unknown applications identified by HSS
Switch
Enables or disables a policy. If the policy is in the Learning complete. Policy not in effect state, you can click
 to enable it. The whitelist policy takes effect only after it is enabled.
to enable it. The whitelist policy takes effect only after it is enabled.Operation
Operations that can be performed on the policy, including:
- Applications. You can click this button to select servers that a policy applies to.
- Edit. You can click this button to modify the period and servers for intelligent learning.
- Delete: You can click this button to delete a whitelist policy.
After a whitelist policy is deleted, the applications on the servers associated to it will no longer be protected.
- Learning
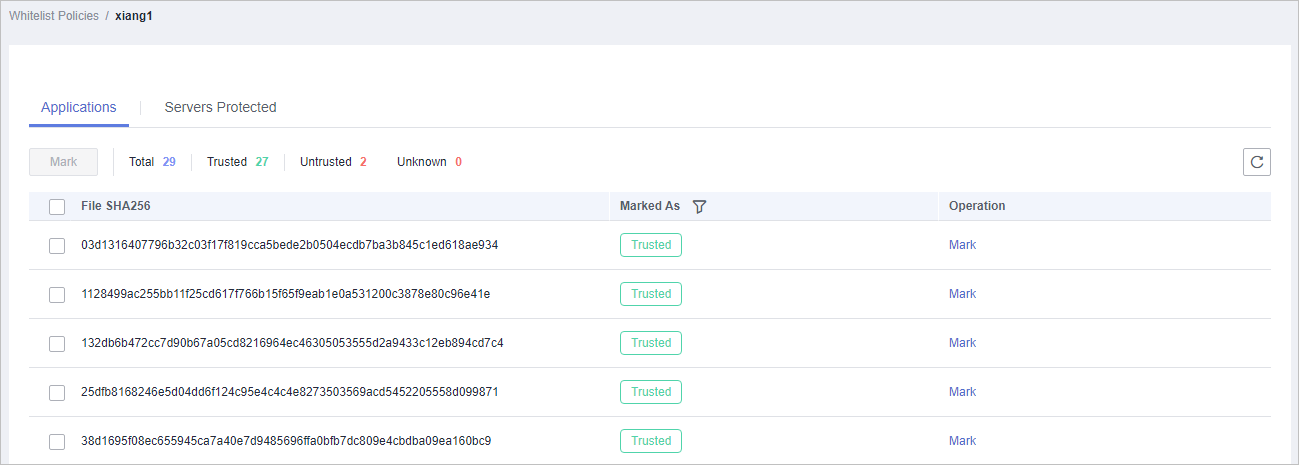
- Click the name of a whitelist policy to view the applications on associated servers, as shown in Figure 2.
The total number of applications, number of trusted applications, number of untrusted applications, and number of unknown applications are displayed. You can mark an application as trusted, untrusted, or unknown, and create an application whitelist for the application.
Figure 2 Application list
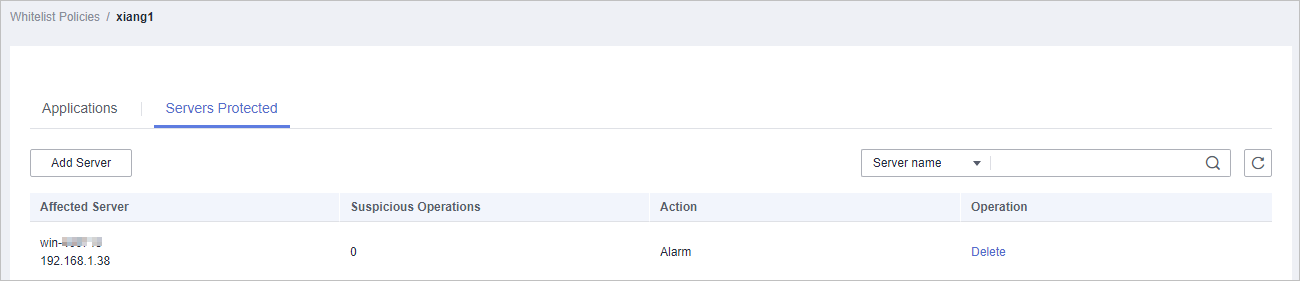
- Click the Servers Protected tab to view the servers that the whitelist policy applies to, as shown in Figure 3.
The server names and IP addresses, whitelist policy, number of suspicious operations, and the way to handle the operations are displayed.
- Suspicious Operations include startup of processes that are not in the whitelist policy or marked as Untrusted or Unknown.
- Action in the following figure indicates that HSS will report an alarm when detecting suspicious operations.
Figure 3 Checking protected servers
 Note
NoteYou can remove servers as required. Servers removed will no longer be protected by the whitelist policy.
- Function Description
- Checking the Whitelist Policy List