Network ACL Overview
Network ACL
A network ACL is an optional layer of protection for your subnets. After you add inbound and outbound rules to a network ACL and associate subnets with it, you can control traffic in and out of the subnets.
A network ACL is different from a security group. A security group protects the instances in it, such as ECSs, databases, and containers, while a network ACL protects the entire subnet. Security groups are a mandatory layer of protection but network ACLs are optional. Network ACLs and security groups can be used together for fine-grained access control.
You need to specify the protocol, source port and address, and destination port and address for each inbound and outbound rule of the network ACL. Suppose you have two subnets in region A, as shown in Figure 1. Subnet-X01 is associated with network ACL Fw-A, and ECSs deployed in this subnet provide web services accessible from the Internet. Subnet-X02 is associated with network ACL Fw-B. Subnet-X02 and Subnet-Y01 are connected through a VPC peering connection. Now, you need to configure inbound and outbound rules to allow ECS-C01 in Subnet-Y01 to remotely log in to ECSs in Subnet-X02.
- Inbound and outbound rules on Fw-A:
Custom inbound rule A01 allows any IP address to access the ECSs in Subnet-X01 through port 80 over TCP or HTTP. If the traffic does not match custom rule A01, the default rule is applied and the traffic is denied to flow into the subnet.
Stateful network ACLs allow responses to inbound requests to leave the subnet without being controlled by rules. The responses from ECSs in Subnet-X01 can go out of the subnet. Other outbound traffic is not allowed to leave Subnet-X01, because the default rule is applied.
- Inbound and outbound rules on Fw-B:
Custom inbound rule B01 allows ECS-C01 in Subnet-Y01 to use access the ECSs in Subnet-X02 through port 22 over TCP or SSH.
Custom outbound rule B02 allows all ICMP traffic over any port. The ping traffic from ECSs in Subnet-X02 to ECS-C01 in Subnet-Y01 can be routed successfully to test the network connectivity.
Figure 1 Network ACL rules
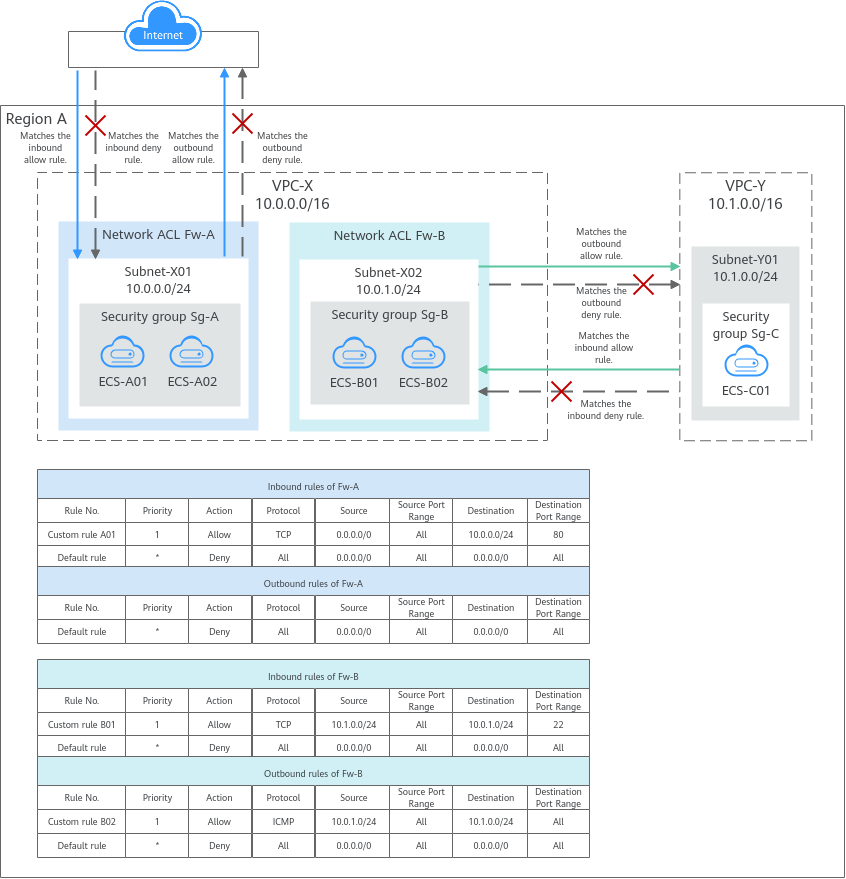
Network ACL Rules
- Network ACL has inbound and outbound rules that are used to control traffic in and out of subnets.
- Inbound rules control traffic sent to the instances in a subnet.
- Outbound rules control traffic from the instances in a subnet to external networks.
- You need to define the protocol, source and destination ports, source and destination IP addresses, and other information for network ACL rules.
- Type: IPv4 or IPv6.
- Action: Allow or Deny. If a request matches a network ACL rule, the action defined in the rule is taken to allow or deny the request.
- Protocol: The protocol to match traffic. The value can be TCP, UDP, or ICMP.
- Source/Destination: The source or destination of the traffic.
- Source Port Range/Destination Port Range: The source or destination ports or port ranges. The value ranges from 1 to 65535.
How Network ACL Rules Work
- After a network ACL is created, you can associate it with one or more subnets to control traffic in and out of the subnets. You can associate a network ACL with multiple subnets. However, a subnet can only be associated with one network ACL.
- Network ACLs use connection tracking to track traffic to and from instances. Changes to inbound and outbound rules do not take effect immediately for the existing traffic.
If you add, modify, or delete a network ACL rule, or associate or disassociate a subnet with or from a network ACL, all the inbound and outbound persistent connections will not be disconnected. New rules will only be applied for the new connections.
After a persistent connection is disconnected, new connections will not be established immediately until the timeout period of connection tracking expires. For example, after an ICMP persistent connection is disconnected, a new connection will be established and a new rule will be applied when the timeout period (30s) expires.
- The timeout period of connection tracking varies by protocol. The timeout period of a TCP connection in the established state is 600s, and that of an ICMP connection is 30s. For other protocols, if packets are received in both inbound and outbound directions, the connection tracking timeout period is 180s. If packets are received only in one direction, the connection tracking timeout period is 30s.
- The timeout period of TCP connections varies by connection status. The timeout period of a TCP connection in the established state is 600s, and that of a TCP connection in the FIN-WAIT state is 30s.
- There are default inbound and outbound rules in network ACLs, as shown in Table 1. If a network ACL has no custom rules, the default inbound and outbound rules are applied, denying all traffic in and out of a subnet. You can use the default rules only when there is no need for traffic to go in and out of a subnet. If the traffic needs to go in and out of the subnet, you need to add custom rules to control traffic as required.
Table 1 Default network ACL rules Direction
Priority
Action
Protocol
Source
Source Port Range
Destination
Destination Port Range
Inbound
*
Deny
All
0.0.0.0/0
All
0.0.0.0/0
All
Outbound
*
Deny
All
0.0.0.0/0
All
0.0.0.0/0
All
- The default and custom rules of a network ACL does not block the traffic described in Table 2.
Table 2 Traffic not blocked by network ACL rules Direction
Description
Inbound
Traffic between the source and destination in the same subnet
Broadcast traffic to 255.255.255.255/32
Multicast traffic to 224.0.0.0/24
Outbound
Traffic between the source and destination in the same subnet
Broadcast traffic to 255.255.255.255/32
Multicast traffic to 224.0.0.0/24
TCP metadata traffic to 169.254.169.254/32 over port 80
Traffic to 100.125.0.0/16 that is reserved for public services on the cloud, such as the DNS server address and NTP server address
How Traffic Matches Network ACL Rules
- Each rule has a priority number. A smaller number indicates a higher priority. A rule with a higher priority is preferentially applied over a rule with a lower priority. The rule with the priority of * is the default rule. It has the lowest priority.
- If multiple network ACL rules conflict, only the rule with the highest priority is applied. If you need a rule to take effect before or after a specific rule, you can insert that rule before or after that specific rule.
A subnet can be associated with one network ACL. If there are multiple rules on the network ACL, rules are applied based on their priority. A smaller number indicates a higher priority. The value of the default rule priority is *, which has the lowest priority.
The matching sequence of inbound traffic is the same as that of outbound traffic. The following takes inbound traffic as an example to describe how the rules are applied.
- If a custom rule is matched:
- If Action is set to Deny, traffic is denied to flow into the subnet.
- If Action is set to Allow, traffic is allowed to flow into the subnet.
- If no custom rule is matched, the default rule is applied, denying traffic to flow into the subnet.
Figure 2 Network ACL matching
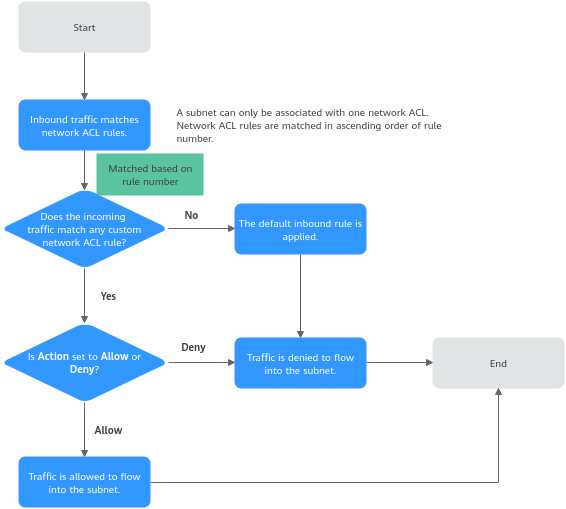
Network ACL Application Scenarios
- If the application layer needs to provide services for external users, traffic from all IP addresses must be allowed to reach the application layer. However, you also need to prevent illegal access from malicious users.
Solution: You can add network ACL rules to deny access from malicious IP addresses.
- Ports with vulnerabilities, for example, port 445 that can be exploited to spread malware like WannaCry ransomware.
Solution: You can add network ACL rules to deny access to a specific port over a specific protocol, for example, access to port 445 over TCP.
- There is no need to control east-west traffic between subnets, but there is a need to control north-south traffic between subnets.
Solution: You can add network ACL rules to control north-south traffic between subnets.
- You may need to adjust the sequence of security rules to improve the access performance to frequently accessed applications.
Solution: A network ACL allows you to adjust the rule sequence so that frequently used rules are applied before other rules.
Network ACL Configuration Procedure
Figure 3 Procedure for configuring a network ACL

No. | Step | Description | Reference |
|---|---|---|---|
1 | Create a network ACL. | A network ACL comes with default inbound and outbound rules that deny traffic in and out of a subnet. The default rules cannot be deleted or modified. | |
2 | Add inbound and outbound rules. | You can add custom rules to control traffic in and out of a subnet. Traffic will be preferentially matched against the custom rules. | |
3 | Associate the network ACL with one or more subnets. | You can associate the network ACL with one or more subnets. If it is enabled, it controls traffic in and out of the subnets. A subnet can be associated with only one network ACL. |
Constraints on Using Network ACLs
- By default, each account can have up to 200 network ACLs in a region.
- A network ACL can contain no more than 20 rules in one direction, or performance will deteriorate.
- Traffic from load balancers is not restricted by network ACL and security group rules if:
Transfer Client IP Address is enabled for the listeners of a load balancer.
The load balancer can still forward traffic to backend servers, even if there is a rule that denies traffic from the load balancer to the backend servers.
- Network ACL
- Network ACL Rules
- How Network ACL Rules Work
- How Traffic Matches Network ACL Rules
- Network ACL Application Scenarios
- Network ACL Configuration Procedure
- Constraints on Using Network ACLs