Creating a LoadBalancer Ingress Using kubectl
This section uses an Nginx workload as an example to describe how to create a LoadBalancer ingress using kubectl.
- If no load balancer is available in the same VPC, CCE can automatically create a load balancer when creating an ingress. For details, see Automatically Creating a Load Balancer While Creating an Ingress.
- If a load balancer is available in the same VPC, perform the operation by referring to Associating an Existing Load Balancer to an Ingress While Creating the Ingress.
Prerequisites
- An available workload has been deployed in the cluster for external access. If no workload is available, deploy a workload by referring to Creating a Deployment, Creating a StatefulSet, or Creating a DaemonSet.
- A Service for external access has been configured for the workload. Services Supported by LoadBalancer Ingresses lists the Service types supported by LoadBalancer ingresses.
- A dedicated load balancer must be of the application type (HTTP/HTTPS) and support private networks (with a private IP address).
Automatically Creating a Load Balancer While Creating an Ingress
The following describes how to run the kubectl command to automatically create a load balancer when creating an ingress.
- Use kubectl to access the cluster. For details, see Accessing a Cluster Using kubectl.
- Create a YAML file named ingress-test.yaml. The file name can be customized.vi ingress-test.yamlNote
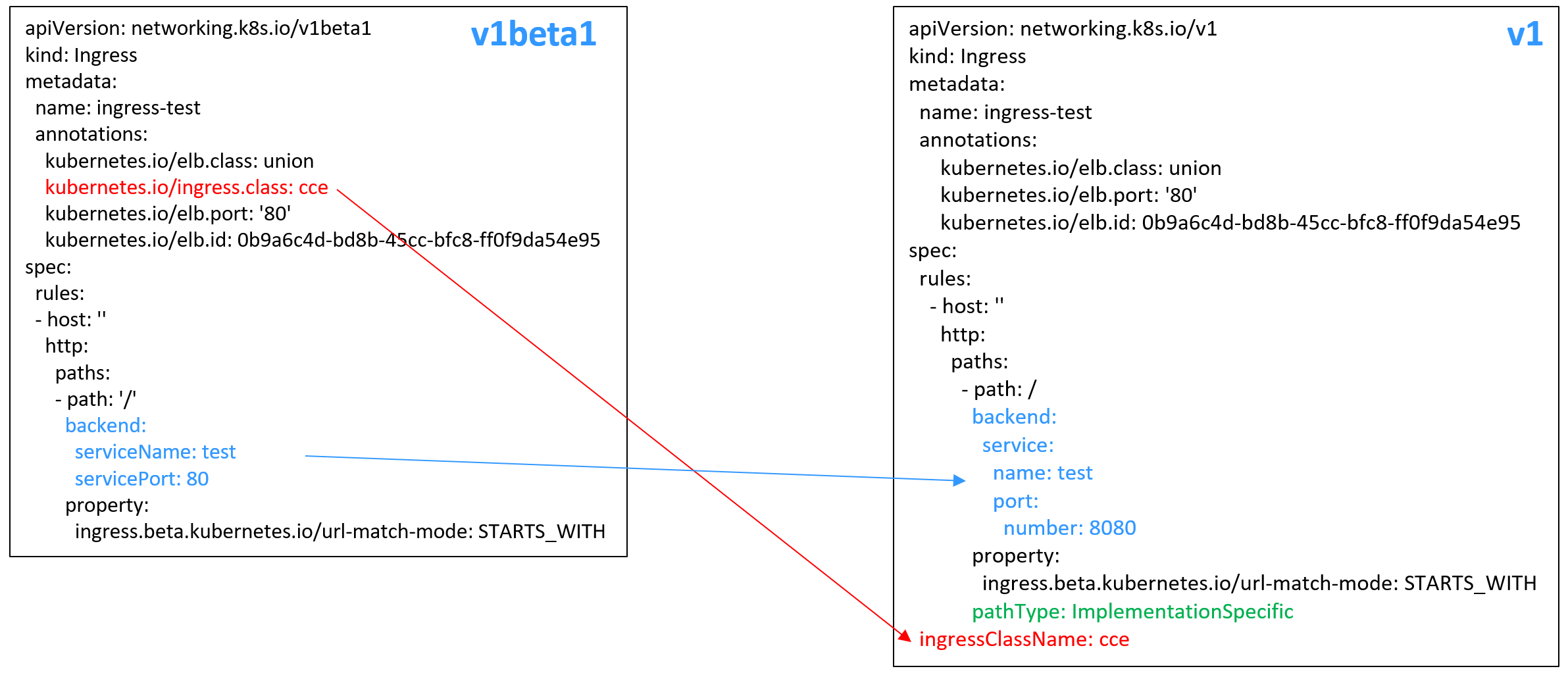
Starting from cluster v1.23, the ingress version is switched from networking.k8s.io/v1beta1 to networking.k8s.io/v1. For details about the differences between v1 and v1beta1, see Ingress API Version Upgrade in CCE Clusters v1.23.
Example of a shared load balancer (public network access) for clusters of v1.23 or later:
apiVersion: networking.k8s.io/v1kind: Ingressmetadata:name: ingress-testannotations:kubernetes.io/elb.class: unionkubernetes.io/elb.port: '80'kubernetes.io/elb.autocreate:'{"type":"public","bandwidth_name":"cce-bandwidth-******","bandwidth_chargemode":"bandwidth","bandwidth_size":5,"bandwidth_sharetype":"PER","vip_subnet_cidr_id": "*****","vip_address": "**.**.**.**","eip_type":"5_bgp"}'kubernetes.io/elb.tags: key1=value1,key2=value2 # ELB resource tagsspec:rules:- host: ''http:paths:- path: '/'backend:service:name: <your_service_name> # Replace it with the name of your target Service.port:number: <your_service_port> # Replace it with the port number of your target Service.property:ingress.beta.kubernetes.io/url-match-mode: STARTS_WITHpathType: ImplementationSpecificingressClassName: cce # A LoadBalancer ingress is used.Example of a shared load balancer (public network access) for clusters of v1.21 or earlier:
apiVersion: networking.k8s.io/v1beta1kind: Ingressmetadata:name: ingress-testannotations:kubernetes.io/elb.class: unionkubernetes.io/ingress.class: cce # A LoadBalancer ingress is used.kubernetes.io/elb.port: '80'kubernetes.io/elb.autocreate:'{"type":"public","bandwidth_name":"cce-bandwidth-******","bandwidth_chargemode":"bandwidth","bandwidth_size":5,"bandwidth_sharetype":"PER","eip_type":"5_bgp"}'kubernetes.io/elb.tags: key1=value1,key2=value2 # ELB resource tagsspec:rules:- host: ''http:paths:- path: '/'backend:serviceName: <your_service_name> # Replace it with the name of your target Service.servicePort: <your_service_port> # Replace it with the port number of your target Service.property:ingress.beta.kubernetes.io/url-match-mode: STARTS_WITHExample of a dedicated load balancer (public network access) for clusters of v1.23 or later:
apiVersion: networking.k8s.io/v1kind: Ingressmetadata:name: ingress-testnamespace: defaultannotations:kubernetes.io/elb.class: performancekubernetes.io/elb.port: '80'kubernetes.io/elb.autocreate:'{"type": "public","bandwidth_name": "cce-bandwidth-******","bandwidth_chargemode": "bandwidth","bandwidth_size": 5,"bandwidth_sharetype": "PER","eip_type": "5_bgp","vip_subnet_cidr_id": "*****","vip_address": "**.**.**.**","elb_virsubnet_ids":["*****"],"available_zone": ["ru-moscow-1a"],"l7_flavor_name": "L7_flavor.elb.s1.small"}'kubernetes.io/elb.tags: key1=value1,key2=value2 # ELB resource tagsspec:rules:- host: ''http:paths:- path: '/'backend:service:name: <your_service_name> # Replace it with the name of your target Service.port:number: <your_service_port> # Replace it with the port number of your target Service.property:ingress.beta.kubernetes.io/url-match-mode: STARTS_WITHpathType: ImplementationSpecificingressClassName: cceExample of a dedicated load balancer (public network access) for clusters of v1.21 or earlier:
apiVersion: networking.k8s.io/v1beta1kind: Ingressmetadata:name: ingress-testnamespace: defaultannotations:kubernetes.io/elb.class: performancekubernetes.io/ingress.class: ccekubernetes.io/elb.port: '80'kubernetes.io/elb.autocreate:'{"type": "public","bandwidth_name": "cce-bandwidth-******","bandwidth_chargemode": "bandwidth","bandwidth_size": 5,"bandwidth_sharetype": "PER","eip_type": "5_bgp","elb_virsubnet_ids":["*****"],"available_zone": ["ru-moscow-1a"],"l7_flavor_name": "L7_flavor.elb.s1.small"}'kubernetes.io/elb.tags: key1=value1,key2=value2 # ELB resource tagsspec:rules:- host: ''http:paths:- path: '/'backend:serviceName: <your_service_name> # Replace it with the name of your target Service.servicePort: <your_service_port> # Replace it with the port number of your target Service.property:ingress.beta.kubernetes.io/url-match-mode: STARTS_WITHTable 1 Key parameters Parameter
Mandatory
Type
Description
kubernetes.io/elb.class
Yes
String
Select a proper load balancer type.
- union: shared load balancer
- performance: dedicated load balancer
kubernetes.io/ingress.class
Yes
(only for clusters of v1.21 or earlier)
String
cce: A proprietary LoadBalancer ingress is used.
This parameter is mandatory when an ingress is created by calling the API.
ingressClassName
Yes
(only for clusters of v1.23 or later)
String
cce: A proprietary LoadBalancer ingress is used.
This parameter is mandatory when an ingress is created by calling the API.
kubernetes.io/elb.port
No
String
This parameter indicates the external port registered with the address of the LoadBalancer Service.
The value ranges from 1 to 65535. The default value is 80 for HTTP and 443 for HTTPS.
NOTE:Some ports on a shared load balancer are highly risky and blocked by default, for example, port 21.
kubernetes.io/elb.subnet-id
None
String
ID of the subnet where the cluster is located. The value can contain 1 to 100 characters.
- Mandatory when a cluster of v1.11.7-r0 or earlier is to be automatically created.
- Optional for clusters later than v1.11.7-r0. It is left blank by default.
kubernetes.io/elb.enterpriseID
No
String
Kubernetes clusters of v1.15 and later versions support this field. In Kubernetes clusters earlier than v1.15, load balancers are created in the default project by default.
ID of the enterprise project in which the load balancer will be created.
The value contains 1 to 100 characters.
How to obtain:
Log in to the management console and choose Enterprise > Project Management on the top menu bar. In the list displayed, click the name of the target enterprise project, and copy the ID on the enterprise project details page.
kubernetes.io/elb.autocreate
Yes
elb.autocreate object
Whether to automatically create a load balancer associated with an ingress. For details about the field description, see Table 2.
Example
- Automatically created dedicated load balancer with an EIP bound:
'{"type":"public","bandwidth_name":"cce-bandwidth-1741230802502","bandwidth_chargemode":"bandwidth","bandwidth_size":5,"bandwidth_sharetype":"PER","eip_type":"5_bgp","available_zone":["*****"],"elb_virsubnet_ids":["*****"],"l7_flavor_name":"L7_flavor.elb.pro.max","l4_flavor_name":"","vip_subnet_cidr_id":"*****"}'
- Automatically created dedicated load balancer with no EIP bound:
'{"type":"inner","available_zone":["*****"],"elb_virsubnet_ids":["*****"],"l7_flavor_name":"L7_flavor.elb.pro.max","l4_flavor_name":"","vip_subnet_cidr_id":"*****"}'
- Automatically created shared load balancer with an EIP bound:
'{"type":"public","bandwidth_name":"cce-bandwidth-1551163379627","bandwidth_chargemode":"bandwidth","bandwidth_size":5,"bandwidth_sharetype":"PER","eip_type":"5_bgp","name":"james"}'
- Automatically created shared load balancer with no EIP bound:
{"type":"inner","name":"A-location-d-test"}
kubernetes.io/elb.tags
No
String
Whether to add resource tags to a load balancer. This function is available only when the load balancer is automatically created, and the cluster is of v1.23.11-r0, v1.25.6-r0, v1.27.3-r0, or later.
A tag is in the format of "key=value". Use commas (,) to separate multiple tags.
host
No
String
Domain name for accessing the Service. By default, this parameter is left blank, and the domain name needs to be fully matched. Ensure that the domain name has been registered and licensed. Once a forwarding policy is configured with a domain name specified, you must use the domain name for access.
path
Yes
String
User-defined route path. All external access requests must match host and path.
NOTE:The access path added here must exist in the backend application. Otherwise, the forwarding fails.
For example, the default access URL of the Nginx application is /usr/share/nginx/html. When adding /test to the ingress forwarding policy, ensure the access URL of your Nginx application contains /usr/share/nginx/html/test. Otherwise, error 404 will be returned.
ingress.beta.kubernetes.io/url-match-mode
No
String
Route matching policy.
Default: STARTS_WITH (prefix match)
Options:
- EQUAL_TO: exact match
- STARTS_WITH: prefix match
- REGEX: regular expression match
pathType
Yes
String
Path type. This field is supported only by clusters of v1.23 or later.
- ImplementationSpecific: The matching method depends on Ingress Controller. The matching method defined by ingress.beta.kubernetes.io/url-match-mode is used in CCE.
- Exact: exact matching of the URL, which is case-sensitive.
- Prefix: prefix matching, which is case-sensitive. With this method, the URL path is separated into multiple elements by slashes (/) and the elements are matched one by one. If each element in the URL matches the path, the subpaths of the URL can be routed normally.NOTE:
- During prefix matching, each element must be exactly matched. If the last element of the URL is the substring of the last element in the request path, no matching is performed. For example, /foo/bar matches /foo/bar/baz but does not match /foo/barbaz.
- When elements are separated by slashes (/), if the URL or request path ends with a slash (/), the slash (/) at the end is ignored. For example, /foo/bar matches /foo/bar/.
See examples of ingress path matching.
Table 2 elb.autocreate data structure Parameter
Mandatory
Type
Description
name
No
String
Name of the automatically created load balancer.
The value can contain 1 to 64 characters. Only letters, digits, underscores (_), hyphens (-), and periods (.) are allowed.
Default: cce-lb+service.UID
type
No
String
Network type of the load balancer.
- public: public network load balancer
- inner: private network load balancer
Default: inner
bandwidth_name
Yes for public network load balancers
String
Bandwidth name. The default value is cce-bandwidth-******.
The value can contain 1 to 64 characters. Only letters, digits, underscores (_), hyphens (-), and periods (.) are allowed.
bandwidth_chargemode
No
String
Bandwidth mode.
- bandwidth: billed by bandwidth
- traffic: billed by traffic
Default: bandwidth
bandwidth_size
Yes for public network load balancers
Integer
Bandwidth size. The value ranges from 1 Mbit/s to 2000 Mbit/s by default. Configure this parameter based on the bandwidth range allowed in your region.
The minimum increment for bandwidth adjustment varies depending on the bandwidth range.
- The minimum increment is 1 Mbit/s if the allowed bandwidth does not exceed 300 Mbit/s.
- The minimum increment is 50 Mbit/s if the allowed bandwidth ranges from 300 Mbit/s to 1000 Mbit/s.
- The minimum increment is 500 Mbit/s if the allowed bandwidth exceeds 1000 Mbit/s.
bandwidth_sharetype
Yes for public network load balancers
String
Bandwidth sharing mode.
- PER: dedicated bandwidth
eip_type
Yes for public network load balancers
String
EIP type.
- 5_bgp: dynamic BGP
The specific type varies with regions. For details, see the EIP console.
vip_subnet_cidr_id
No
String
The ID of the IPv4 subnet where the load balancer resides. This subnet is used to allocate IP addresses for the load balancer to provide external services. The IPv4 subnet must belong to the cluster's VPC.
If this parameter is not specified, the load balancer and the cluster will be in the same subnet by default.
This field can be specified only for clusters of v1.21 or later.
How to Obtain
Log in to the VPC console. In the navigation pane, choose Subnets. Filter the target subnet by the cluster's VPC name, click the subnet name, and copy the IPv4 Subnet ID on the Summary tab page.
ipv6_vip_virsubnet_id
No
String
The ID of the IPv6 subnet where the load balancer is deployed. IPv6 must be enabled for the subnet.
This parameter is available only for dedicated load balancers.
How to Obtain
Log in to the VPC console. In the navigation pane, choose Subnets. Filter the target subnet by the cluster's VPC name, click the subnet name, and copy the Network ID on the Summary tab page.
elb_virsubnet_ids
No
Array of strings
The network ID of the subnet where the load balancer is located. This subnet is used to allocate IP addresses for accessing the backend server. If this parameter is not specified, the subnet specified by vip_subnet_cidr_id will be used by default. Load balancers occupy varying numbers of subnet IP addresses based on their specifications. Do not use the subnet CIDR blocks of other resources (such as clusters or nodes) as the load balancer's CIDR block.
This parameter is available only for dedicated load balancers.
Example:
"elb_virsubnet_ids": ["14567f27-8ae4-42b8-ae47-9f847a4690dd"]How to Obtain
Log in to the VPC console. In the navigation pane, choose Subnets. Filter the target subnet by the cluster's VPC name, click the subnet name, and copy the Network ID on the Summary tab page.
vip_address
No
String
Private IP address of the load balancer. Only IPv4 addresses are supported.
The IP address must be in the ELB CIDR block. If this parameter is not specified, an IP address will be automatically assigned from the ELB CIDR block.
This parameter is available only in clusters of v1.23.11-r0, v1.25.6-r0, v1.27.3-r0, or later versions.
available_zone
Yes
Array of strings
AZ where the load balancer is located.
This parameter is available only for dedicated load balancers.
l4_flavor_name
No
String
Flavor name of the layer-4 load balancer. This parameter is mandatory when TCP or UDP is used.
- Elastic: applies to fluctuating traffic, billed based on total traffic. Clusters of v1.21.10-r10, v1.23.8-r10, v1.25.3-r10, and later versions support elastic specifications.
- Fixed: applies to stable traffic, billed based on specifications.
This parameter is available only for dedicated load balancers.
l7_flavor_name
No
String
Flavor name of the layer-7 load balancer. This parameter is mandatory when HTTP is used.
- Elastic: applies to fluctuating traffic, billed based on total traffic. Clusters of v1.21.10-r10, v1.23.8-r10, v1.25.3-r10, and later versions support elastic specifications.
- Fixed: applies to stable traffic, billed based on specifications.
This parameter is available only for dedicated load balancers. Its value must match that of l4_flavor_name, meaning both must be either elastic specifications or fixed specifications.
- Create an ingress.kubectl create -f ingress-test.yaml
If information similar to the following is displayed, the ingress has been created:
ingress/ingress-test created - Check the created ingress.kubectl get ingress
If information similar to the following is displayed, the ingress has been created:
NAME CLASS HOSTS ADDRESS PORTS AGEingress-test cce * 121.**.**.** 80 10s - Enter http://121.**.**.**:80 in the address box of the browser to access the workload (for example, Nginx workload).
121.**.**.** indicates the IP address of the unified load balancer.
Associating an Existing Load Balancer to an Ingress While Creating the Ingress
CCE allows you to connect to an existing load balancer when creating an ingress.
- Use kubectl to access the cluster. For details, see Accessing a Cluster Using kubectl.
- Create a YAML file named ingress-test.yaml. The file name can be customized.vi ingress-test.yamlNote
- Starting from cluster v1.23, the ingress version is switched from networking.k8s.io/v1beta1 to networking.k8s.io/v1. For details about the differences between v1 and v1beta1, see Ingress API Version Upgrade in CCE Clusters v1.23.
- An existing dedicated load balancer must be of the application type (HTTP/HTTPS) and support private networks (with a private IP address).
If the cluster version is 1.23 or later, the YAML file configuration is as follows:
apiVersion: networking.k8s.io/v1kind: Ingressmetadata:name: ingress-testannotations:kubernetes.io/elb.id: <your_elb_id> # Replace it with the ID of your existing load balancer.kubernetes.io/elb.ip: <your_elb_ip> # Replace it with the IP of your existing load balancer.kubernetes.io/elb.class: performance # Load balancer typekubernetes.io/elb.port: '80'spec:rules:- host: ''http:paths:- path: '/'backend:service:name: <your_service_name> # Replace it with the name of your target Service.port:number: 8080 # Replace 8080 with the port number of your target Service.property:ingress.beta.kubernetes.io/url-match-mode: STARTS_WITHpathType: ImplementationSpecificingressClassName: cceIf the cluster version is 1.21 or earlier, the YAML file configuration is as follows:
apiVersion: networking.k8s.io/v1beta1kind: Ingressmetadata:name: ingress-testannotations:kubernetes.io/elb.id: <your_elb_id> # Replace it with the ID of your existing load balancer.kubernetes.io/elb.ip: <your_elb_ip> # Replace it with the IP of your existing load balancer.kubernetes.io/elb.class: performance # Load balancer typekubernetes.io/elb.port: '80'kubernetes.io/ingress.class: ccespec:rules:- host: ''http:paths:- path: '/'backend:serviceName: <your_service_name> # Replace it with the name of your target Service.servicePort: 80property:ingress.beta.kubernetes.io/url-match-mode: STARTS_WITHTable 3 Key parameters Parameter
Mandatory
Type
Description
kubernetes.io/elb.id
No
String
ID of a load balancer. The value can contain 1 to 100 characters.
Use either this parameter or kubernetes.io/elb.ip. If they conflict, kubernetes.io/elb.id will take precedence.
How to obtain:
On the management console, click Service List, and choose Networking > Elastic Load Balance. Click the name of the target load balancer. On the Summary tab page, find and copy the ID.
kubernetes.io/elb.ip
No
String
Service address of a load balancer. The value can be the public IP address of a public network load balancer or the private IP address of a private network load balancer.
Use either this parameter or kubernetes.io/elb.id. If they conflict, kubernetes.io/elb.id will take precedence.
kubernetes.io/elb.class
Yes
String
Load balancer type.
- union: shared load balancer
- performance: dedicated load balancer, which can be used only in clusters of v1.17 and later.
NOTE:If a LoadBalancer ingress accesses an existing dedicated load balancer, the dedicated load balancer must be of the application load balancing (HTTP/HTTPS) type.
- Create an ingress.kubectl create -f ingress-test.yaml
If information similar to the following is displayed, the ingress has been created:
ingress/ingress-test created - Check the created ingress.kubectl get ingress
If information similar to the following is displayed, the ingress has been created:
NAME CLASS HOSTS ADDRESS PORTS AGEingress-test cce * 121.**.**.** 80 10s - Enter http://121.**.**.**:80 in the address box of the browser to access the workload (for example, Nginx workload).
121.**.**.** indicates the IP address of the unified load balancer.
- Ingress API Version Upgrade in CCE Clusters v1.23
- Prerequisites
- Automatically Creating a Load Balancer While Creating an Ingress
- Associating an Existing Load Balancer to an Ingress While Creating the Ingress