Scenarios
A security group consists of inbound and outbound rules to control the traffic that is allowed to flow into or out of instances (such as ECSs) in the security group. Security group rules are commonly used to allow or deny network traffic from specific sources or over specific protocols, block certain ports, and define specific access permissions for instances.
Precautions
Before adding a security group rule, note the following:
- A security group has inbound and outbound rules to control traffic that is allowed to reach or leave the instances associated with the security group. For details about the rules, see What Are Security Group Rules?
- If an instance is associated with multiple security groups, the traffic matches security group rules by priority. For details about the matching sequence, see How Traffic Matches Security Group Rules.
- The number of rules in a security group is limited. Keep only the rules you need. For details, see Constraints on Using Security Groups.
- After allowing traffic over a port in a security group rule, you need to ensure that the port used by the instance is also opened. For details, see Checking Whether a Port Is Enabled on an ECS.
- By default, instances in the same security group can communicate with each other. If instances in the same security group cannot communicate with each other, possible causes are as follows:
- The inbound rules for communications between these instances are deleted. Table 1 shows the inbound rules.
Table 1 Inbound rules for communication between instances Direction
Priority
Action
Type
Protocol & Port
Source/Destination
Inbound
1
Allow
IPv4
All
Source: current security group (Sg-A)
Inbound
1
Allow
IPv6
All
Source: current security group (Sg-A)
- Different VPCs cannot communicate with each other. The instances belong to the same security group but different VPCs.
You can use VPC peering connections to connect different VPCs.
- The inbound rules for communications between these instances are deleted. Table 1 shows the inbound rules.
Configuration Example
Before configuring security group rules, you need to plan access policies for instances in the security group.
- If an instance needs to provide services for external systems, add an inbound rule to allow external requests to the instance.
- If there are attacks to an instance from external networks, add an inbound rule to deny external requests that have security risks.
- If an instance needs to access the Internet, add an outbound rule to allow requests from the instance to the Internet.
- If you no longer need to control certain inbound or outbound traffic, you can delete the corresponding security group rules to simplify the rule configuration.
Security Group Examples shows more security group rule configuration examples.
Checking Whether a Port Is Enabled on an ECS
After allowing traffic over a port in a security group rule, you need to ensure that the port used by the instance is also opened.
For example, if you have deployed a website on an ECS and want users to access your website through HTTP (80), you need to add an inbound rule to the ECS security group to allow access over the port. Table 5 shows the rule.
Direction | Priority | Action | Type | Protocol & Port | Source |
|---|---|---|---|---|---|
Inbound | 1 | Allow | IPv4 | TCP: 80 | IP address: 0.0.0.0/0 |
After adding the security group rule, perform the following operations to check whether the ECS port is opened and whether the rule is applied:
- Log in to the ECS and check whether the ECS port is enabled.
- Checking a Linux ECS port
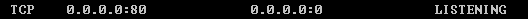
Run the following command to check whether TCP port 80 is being listened on:
netstat -an | grep 80
If the following figure is displayed, TCP port 80 is enabled.
Figure 1 Command output for the Linux ECS

- Checking a Windows ECS port
- Choose Start > Run. Type cmd to open the Command Prompt.
- Run the following command to check whether TCP port 80 is being listened on:
netstat -an | findstr 80
If the following figure is displayed, TCP port 80 is enabled.
Figure 2 Command output for the Windows ECS
- Checking a Linux ECS port
- Enter http://ECS EIP in the address box of the browser and press Enter.
If the requested page can be accessed, the security group rule has taken effect.



