As an administrator, you can create user groups and grant them permissions using policies or roles. Users added to the user groups inherit permissions from the user groups. IAM provides general permissions (such as administrator or read-only permissions) for each cloud service, which you can assign to user groups. Users in the groups can then use cloud services based on the assigned permissions. For details, see Assigning Permissions to an IAM User. To learn about system-defined permissions of all cloud services, see "Permissions".
Prerequisites
Before creating a user group, learn about the following:
- Basic concepts of permissions
- Permissions provided by IAM
Creating a User Group
- Log in to the IAM console as the administrator.
- Choose User Groups from the navigation pane, and click Create User Group in the upper right corner.
Figure 1 Creating a user group
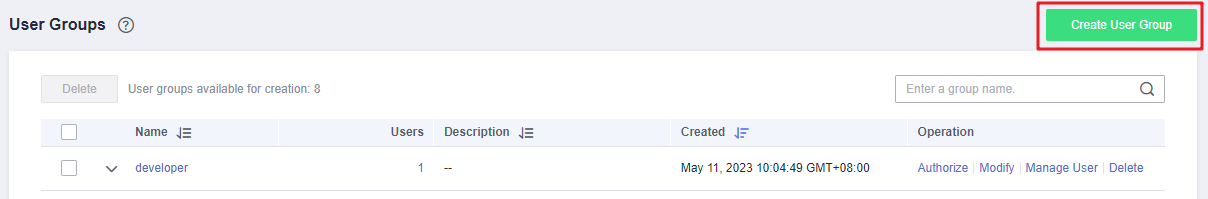
- On the displayed page, enter a user group name.
- Click OK.Note
You can create a maximum of 20 user groups. To create more user groups, increase the quota by referring to How Do I Increase My Quota?
Assigning Permissions to a User Group
To assign permissions to a user group, perform the operations below. To revoke permissions of a user group, see Managing Permissions of a User Group.
- In the user group list, locate the created user group click Authorize in the Operation column.
Figure 2 Going to the user group authorization page
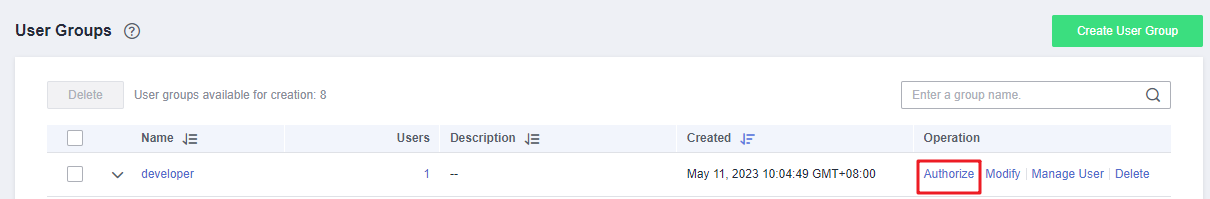
- On the Authorize User Group page, select the permissions to be assigned to the user group and click Next.
If the system-defined policies do not meet your requirements, click Create Policy in the upper right corner to create custom policies. You can use them to supplement system-defined policies for refined permissions control. For details, see Creating a Custom Policy.
Figure 3 Selecting permissions
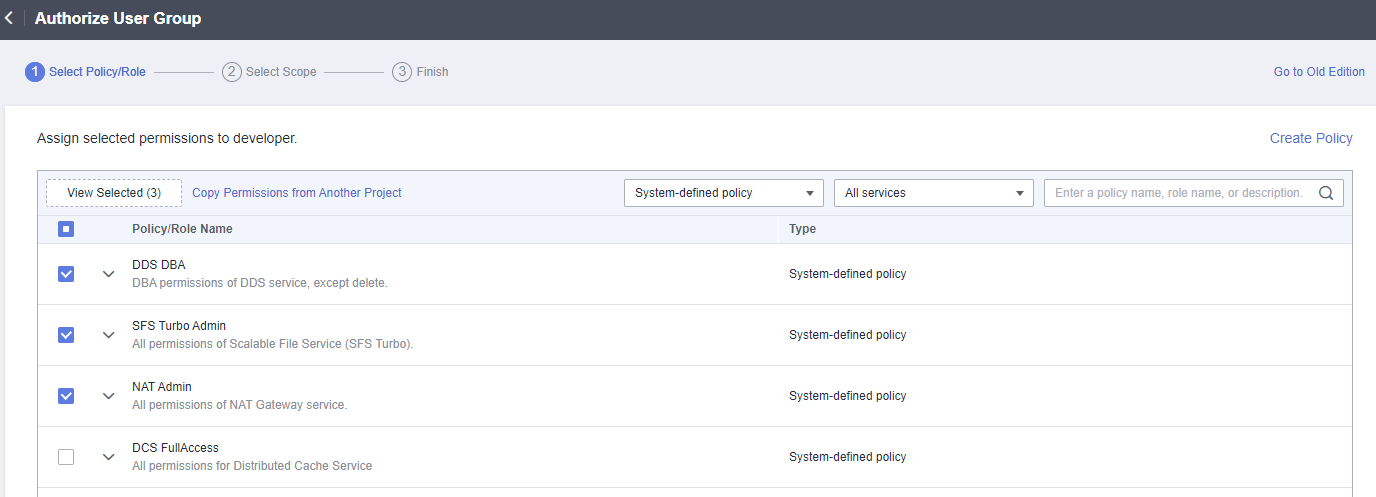
- Specify the scope. The system automatically recommends an authorization scope for the permissions you selected. Table 1 describes all the authorization scopes provided by IAM.
Table 1 Authorization scopes Scope
Description
All resources
IAM users will be able to use all resources, including those in enterprise projects, region-specific projects, and global services under your account based on assigned permissions.
Enterprise projects
IAM users can use the resources in the enterprise projects you select based on the assigned permissions. This option is available only when Enterprise Project is enabled.
For details about enterprise projects, see "Enterprise Management" in the Enterprise Management User Guide.
Region-specific projects
IAM users can use the resources in the region-specific projects you select based on the assigned permissions.
If you select global service permissions, the permissions will be applied to all resources by default. If you select project-level service permissions, the permissions will be applied to the region-specific projects you select.
Global services
IAM users can use global services based on the assigned permissions. Global services are deployed for all physical regions. IAM users do not need to specify a region when accessing these services, such as Object Storage Service (OBS) and Content Delivery Network (CDN).
If you select project-level service permissions, the permissions will be applied to all resources by default. If you select global service permissions, the permissions will be applied to the global services.
- Click OK.
Table 2 lists the common permissions. For all service-specific permissions, see Permission Description.
- If you add an IAM user to multiple groups, the user will inherit all the permissions from these groups.
Category | Policy/Role Name | Description | Authorization Scope |
|---|---|---|---|
General administration | FullAccess | Full permissions for services supporting policy-based access control. | All resources |
Resource management | Tenant Administrator | Administrator permissions for all services except IAM. | All resources |
Viewing resources | Tenant Guest | Read-only permissions for all resources. | All resources |
IAM user management | Security Administrator | Administrator permissions for IAM. | Global services |
Computing O&M | ECS Admin | Administrator permissions for ECS. | Region-specific projects |
CCE FullAccess | Administrator permissions for Cloud Container Engine (CCE). | Region-specific projects | |
BMS FullAccess | Administrator permissions for Bare Metal Server (BMS). | Region-specific projects | |
IMS Admin | Administrator permissions for Image Management Service (IMS). | Region-specific projects | |
AutoScaling FullAccess | Administrator permissions for Auto Scaling (AS). | Region-specific projects | |
Network O&M | VPC Admin | Administrator permissions for Virtual Private Cloud (VPC). | Region-specific projects |
ELB Admin | Administrator permissions for Elastic Load Balance (ELB). | Region-specific projects | |
Database O&M | RDS FullAccess | Administrator permissions for Relational Database Service (RDS). | Region-specific projects |
DDS FullAccess | Administrator permissions for Document Database Service (DDS). | Region-specific projects | |
DDM FullAccess | Administrator permissions for Distributed Database Middleware (DDM). | Region-specific projects | |
Security O&M | WAF Administrator | Administrator permissions for Web Application Firewall (WAF). | Region-specific projects |
KMS Administrator | Administrator permissions for Key Management Service (KMS), which has been renamed Data Encryption Workshop (DEW). | Region-specific projects | |
DBSS FullAccess | Administrator permissions for Database Security Service (DBSS). | Region-specific projects |