How ELB Works
Overview
Figure 1 Working mechanism
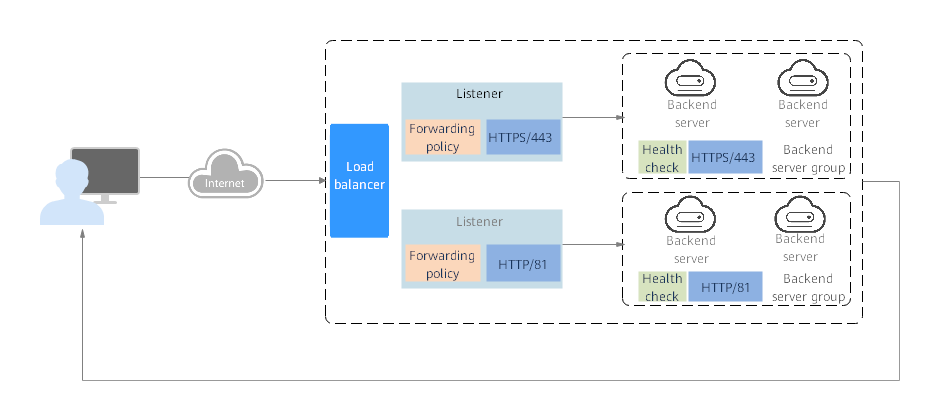
The following describes how ELB works:
- A client sends a request to your application.
- The listeners added to your load balancer use the protocols and ports you have configured to receive the request.
- The listener forwards the request to the associated backend server group based on your configuration. If you have configured a forwarding policy for the listener, the listener evaluates the request based on the forwarding policy. If the request matches the forwarding policy, the listener forwards the request to the backend server group configured for the forwarding policy.
- Healthy backend servers in the backend server group receive the request based on the load balancing algorithm and the routing rules you specify in the forwarding policy, handle the request, and return a result to the client.
How requests are routed depends on the load balancing algorithms configured for each backend server group. If the listener uses HTTP or HTTPS, how requests are routed also depends on the forwarding policies configured for the listener.
Load Balancing Algorithms
Dedicated load balancers support four load balancing algorithms: weighted round robin, weighted least connections, source IP hash, and connection ID.
Shared load balancers support weighted round robin, weighted least connections, and source IP hash algorithms.
Weighted Round Robin
Figure 2 shows an example of how requests are distributed using the weighted round robin algorithm. Two backend servers are in the same AZ and have the same weight, and each server receives the same proportion of requests.
Figure 2 Traffic distribution using the weighted round robin algorithm
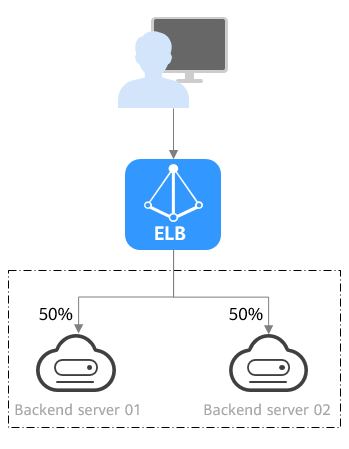
Description | Requests are routed to backend servers in sequence based on their weights. Backend servers with higher weights receive proportionately more requests, whereas equal-weighted servers receive the same number of requests. |
|---|---|
When to Use | This algorithm is typically used for short connections, such as HTTP connections.
|
Disadvantages |
|
Weighted Least Connections
Figure 3 shows an example of how requests are distributed using the weighted least connections algorithm. Two backend servers are in the same AZ and have the same weight, 100 connections have been established with backend server 01, and 50 connections have been established with backend server 02. New requests are preferentially routed to backend server 02.
Figure 3 Traffic distribution using the weighted least connections algorithm
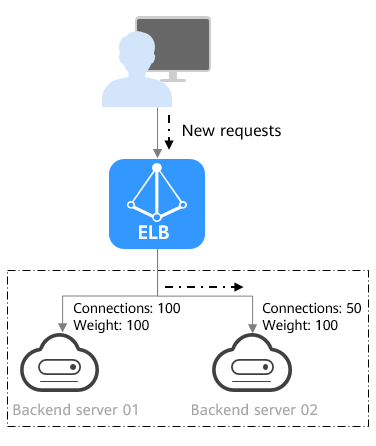
Description | Requests are routed to the server with the lowest connections-to-weight ratio. In addition to the number of connections, each server is assigned a weight based on its capacity. Requests are routed to the server with the lowest connections-to-weight ratio. |
|---|---|
When to Use | This algorithm is often used for persistent connections, such as connections to a database.
|
Disadvantages |
|
Source IP Hash
Figure 4 shows an example of how requests are distributed using the source IP hash algorithm. Two backend servers are in the same AZ and have the same weight. If backend server 01 has processed a request from IP address A, the load balancer will route new requests from IP address A to backend server 01.
Figure 4 Traffic distribution using the source IP hash algorithm

Description | The source IP hash algorithm calculates the source IP address of each request and routes requests from the same IP address to the same backend server. |
|---|---|
When to Use | This algorithm is often used for applications that need to maintain user sessions or state.
|
Disadvantages |
|
- Overview
- Load Balancing Algorithms
- Weighted Round Robin
- Weighted Least Connections
- Source IP Hash