Creating a Doris Cluster
You can centrally manage clusters with CloudTable. A cluster is necessary for using CloudTable. This section describes how to create a cluster on the CloudTable console.
Prerequisites
- The VPC and security group of the cluster to be created must be the same as those of the ECS on the public network. Otherwise, the client cannot access the cluster.
- Before creating a cluster, you must configure inbound security group rules. For details, see "Configuring Security Group Rules" in the Elastic Cloud Server User Guide.
- Before creating a cluster, you must add the ICMP protocol to the security group rules so that you can view the status of each node by pinging the node IP address on the management plane. For details, see "Configuring Security Group Rules" in the Elastic Cloud Server User Guide.
Procedure
- Log in to the CloudTable console.
- Select a region in the upper left corner.
- Click Buy Cluster in the upper right corner.
- Configure basic cluster information by referring to the following table.
Table 1 Region Parameter
Description
Region
Current working zone of the cluster.
- Select the region for the cluster nodes to run.
AZ
Select the AZ associated with the cluster's region.
Billing Mode
Select Pay-per-use.
Table 2 Cluster and network configuration Parameter
Description
Name
Name of a cluster.
The cluster name must consist of 4 to 32 characters and must begin with a letter. It may include only letters, digits, and hyphens (-) but must not contain any other special characters. Additionally, the cluster name is case-insensitive.
VPC
A Virtual Private Cloud (VPC) is a secure, isolated, logical network environment.
Retain the default settings. If there is no available VPC, click View VPC to access the VPC console and create a VPC.
Subnet
Specify a VPC subnet.
A subnet provides dedicated network resources that are isolated from other networks, improving network security.
Security Group
A security group is used to control ECS access within a security group or between security groups by defining access rules. You can define different access control rules for a security group. These rules can specify which ECS ports or protocols are accessible and can be used to control inbound and outbound network traffic of VMs. After an ECS is added to the security group, it is protected by these access control rules. ECSs that do not belong to the security group cannot communicate with ECSs in the security group.
You can use an existing security group or click View Security Group to create a new one.
For more information about security groups, see Security > Security Group > Security Group Overview.
Database Engine
Select the type of cluster to be created.
Doris Kernel
Engine version of the component.
Figure 1 FE node configuration
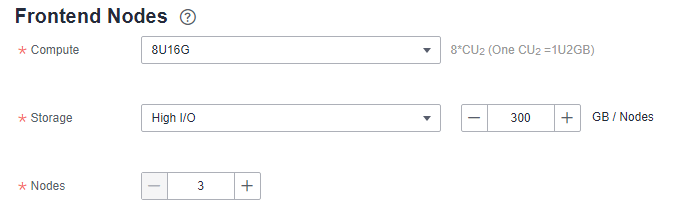
Table 3 FE node configuration parameters Parameter
Description
Compute
Select proper compute specifications based on service requirements. Each specification displays the CPU, memory, and recommended application scenarios of a single node.
NOTE:Available computing specifications:
- 8U16G
- 16U32G
- 32U64G
- 64U128G
- 4U16G
- 8U32G
- 16U64G
- 32U128G
- 64U256G
Storage
Select the disk specifications and capacity of the Doris compute node.
NOTE:- Available storage specifications:
- High I/O
- Ultra-high I/O
- Extreme SSD
- The capacity ranges from 200 GB to 2,000 GB per node.
Nodes
Specify the number of nodes in the cluster.
You can add 3 to 5 FE nodes.
Table 4 BE node configuration (EVS) Parameter
Description
Compute
Select proper compute specifications based on service requirements. Each specification displays the CPU, memory, and recommended application scenarios of a single node.
NOTE:Available computing specifications:
- 4 vCPUs and 16 GB memory (It is advised to utilize this specification solely for functional testing purposes. For deployment in a production environment, a configuration with 8 vCPUs and 32 GB memory or higher is recommended.)
- 8U16G
- 16U32G
- 32U64G
- 64U128G
- 8U32G
- 16U64G
- 32U128G
- 64U256G
Storage
Select the disk specifications and capacity of the Doris compute node.
NOTE:- Available storage specifications:
- High I/O
- Ultra-high I/O
- Extreme SSD
- The capacity ranges from 400 GB to 10,000 GB per node.
Nodes
Specify the number of nodes in the cluster.
You can add 3 to 100 BE nodes.
Table 5 Password setting parameters Parameter
Description
Enterprise Project
You can group related cloud resources (for example, resources used for the same purpose) and manage them by enterprise project.
NOTE:- You can delete a user that was authorized to manage an enterprise project if the enterprise's business has changed and the user should not have the permissions to manage the enterprise project.
- You can delete a user or multiple users.
- After a user that was authorized to manage an enterprise project is deleted, the user cannot manage the enterprise project. If the user needs to manage the enterprise project, authorize the user to manage the enterprise project again.
Username
Doris management user, which is used to connect to the Doris cluster. The default value is admin and cannot be changed.
Password
Set the password of the admin user.
The password complexity requirements are as follows:
- The password must contain 8 to 12 characters.
- The password must contain at least four types of the following characters: uppercase and lowercase letters, digits, and special characters ($@!%*?&).
- The password cannot be the same as the username or the username spelled backwards.
- The strong and weak password check should be performed.NOTE:
Change the password regularly and keep it secure.
Confirm Password
Enter the password of the admin user again for confirmation.
Broker Process
Whether to enable the Broker process, which is used to import data for customers. After the cluster is created, this process cannot be enabled.
Enable Https
Whether to enable HTTPS access channel encryption. The HTTPS port number is 8050.
NOTE:- When HTTPS is enabled, only the MySQL 8.0 or later client can be used to connect to the cluster. The connection port is 9030. For details, see Connecting to a Doris Cluster.
- The HTTPS option is enabled during cluster creation and cannot be disabled later.
- If the HTTPS option is not enabled during cluster creation, it cannot be enabled later.
Enable Interface Authentication
After this function is enabled, account and password authentication needs to be added for REST APIs within the cluster. This may marginally impact performance.
NOTE:- This parameter is displayed when Enable Https is toggled on.
- After this option is enabled, you need to add account and password authentication when using REST APIs in the Doris cluster, such as APIs for modifying parameters and obtaining cluster monitoring data.
- Set the parameters and click Buy Now.
- On the displayed page, confirm the cluster specification order information and click Submit. The cluster creation task is submitted.
- Click Back to Cluster List to view the cluster status.
The cluster creation task takes some time. The initial status of the cluster is Creating. After the cluster is created, the cluster status changes to In service.
- Prerequisites
- Procedure