CFW protects Internet border traffic by protecting EIPs. After EIP protection is enabled, your service traffic will pass through CFW. By default, all traffic is allowed.
After protection is enabled, you can configure access control policies or the IPS protection mode. CFW will check traffic and block or allow traffic based on your configuration.
For more information, see Adding a Protection Rule. For details about IPS, see Configuring an IPS Policy.
What Is Internet Border Traffic?
Internet border traffic, a type of north-south traffic, is exchanged between cloud assets and the Internet. It includes inbound traffic (from the Internet to cloud assets) and outbound traffic (from cloud assets to the Internet).
Figure 1 Internet border traffic protection
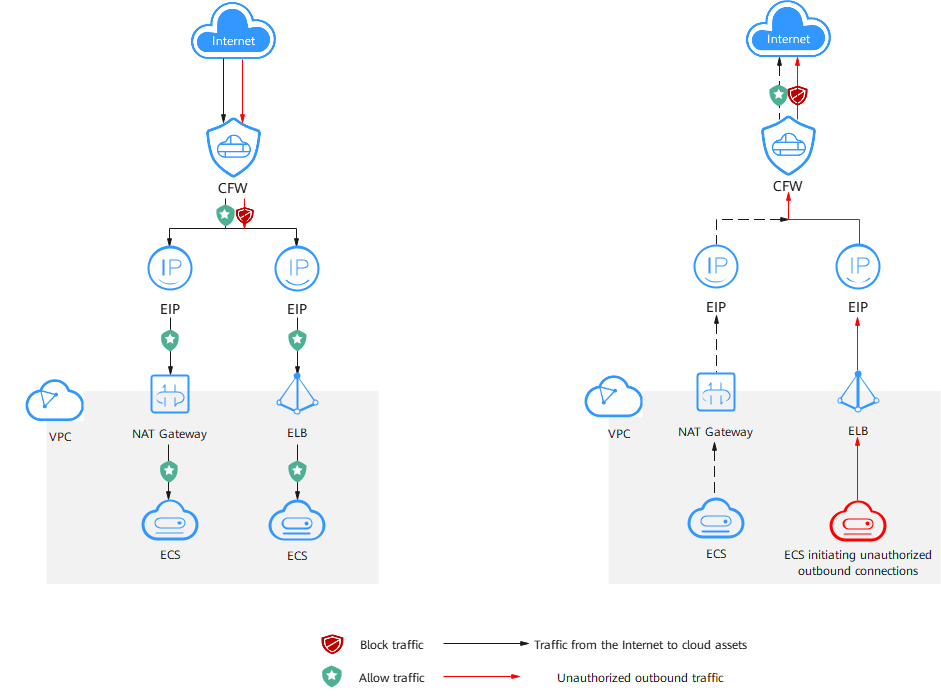
Protected Objects
ECSs, NAT gateways, ELBs, and other resources bound to EIPs.
Constraints
- Currently, IPv6 addresses cannot be protected.
- An EIP can only be protected by one firewall.
Impacts on Services
Before enabling EIP protection, check whether there is any protection rule or blacklist that blocks all traffic.
- If protection is enabled for an EIP, such a protection rule or blacklist will take effect and block all the traffic of the EIP. This may interrupt services. Before enabling protection, check for persistent connections and services that do not support session reestablishment. If any, handle them first.
For details about how to edit a protection rule, see Managing Protection Rules. For details about how to edit a blacklist, see Managing the Blacklist and the Whitelist.
- If no protection rule or blacklist is configured to block all traffic, enabling or disabling EIP protection will not interrupt services.
Enabling Internet Border Traffic Protection
- Log in to the management console.
- Click
 in the upper left corner of the management console and select a region or project.
in the upper left corner of the management console and select a region or project. - In the navigation pane on the left, click
 and choose . The Dashboard page will be displayed.
and choose . The Dashboard page will be displayed. - (Optional) Switch to another firewall instance. Select a firewall from the drop-down list in the upper left corner of the page.
- In the navigation pane, choose . The EIPs page is displayed. The EIP information is automatically updated to the list.
- Enable EIP protection.
IPv6 protection is not supported for EIPs. An EIP can be protected by only one firewall.
- Enable protection for a single EIP: In the row of the EIP, click Enable Protection in the Operation column.
- Enable protection for multiple EIPs: Select the EIPs that you want to enable protection and click Enable Protection above the list.
- On the page that is displayed, check the information and click Bind and Enable. Then the Protection Status changes to Protected.
After protection is enabled for an EIP, the system allows all traffic by default. That is, the default action of the access control policy is Allow.
Auto-protecting New EIPs
If auto-protection on new EIPs is enabled, CFW automatically synchronizes EIPs on the hour and enables protection for new EIPs. The traffic of the EIPs will be protected by the firewall.
How to enable: Go to the Assets > EIPs page of CFW and enable Auto Protect New EIP.
Follow-up Operations
- For details about how to view the traffic trend and statistics of CFW, see Traffic Analysis. For details about traffic records, see Traffic Logs.
- After protection is enabled, all traffic is allowed by default. CFW will block traffic based on the policies you configure.
Table 1 Configuring a policy Purpose
Operation Guide
Control traffic
You can configure protection policies to control traffic.
- Allow or block traffic based on protection rules.
- Traffic allowing rule: The allowed traffic will be checked by functions such as intrusion prevention system (IPS) and antivirus.
- Traffic blocking rule: Traffic will be directly blocked.
- Allow or block traffic based on the blacklist and whitelist:
- Whitelist: Traffic will be directly allowed without being checked by other functions.
- Blacklist: Traffic will be directly blocked.
Block network attacks
You can configure intrusion prevention. For details, see Configuring Intrusion Prevention.
- Allow or block traffic based on protection rules.
Related Operations
- Disabling EIP protectionCaution
If EIP protection is disabled, CFW no longer protects the EIP traffic, and EIPs may be exposed to attacks. Exercise caution when performing this operation.
- To disable an EIP, click Disable Protection in the column of the EIP.
- To disable multiple EIPs, select them and click Disable Protection above the table.
- Exporting the EIP list: Click Export above the list and select an export scope.
- What Is Internet Border Traffic?
- Protected Objects
- Constraints
- Impacts on Services
- Enabling Internet Border Traffic Protection
- Auto-protecting New EIPs
- Follow-up Operations
- Related Operations