Cloud Firewall (CFW) is a next-generation cloud-native firewall. It protects the Internet border and VPC border on the cloud by real-time intrusion detection and prevention, global unified access control, full traffic analysis, log audit, and tracing. It employs AI for intelligent defense, and can meet changing business needs, helping you easily handle security threats. CFW is a basic service that provides network security protection for user services on the cloud.
- Internet border: The border between cloud assets and the Internet. It controls the inbound (from the Internet to the cloud) and outbound (from the cloud to the Internet) traffic.
- VPC border: The border between a VPC and an on-premises integrated data center (IDC), or between two VPCs. It controls internal service access.
Positioning
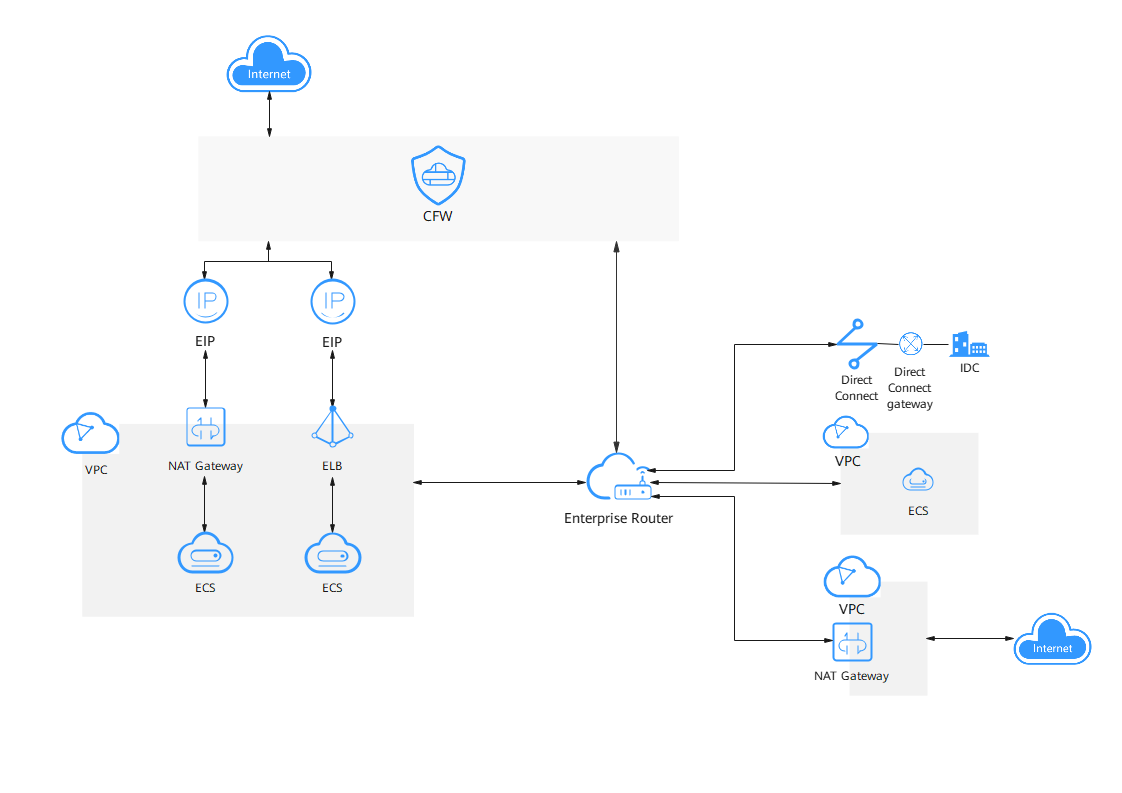
Protected Objects
Protection Type | Protected Object | Reference |
|---|---|---|
Internet border | Elastic IPs (EIPs). The Elastic Cloud Servers (ECSs), NAT gateways, Elastic Load Balance (ELB), or other resources that are bound to EIPs can be protected. | |
VPC border | Virtual Private Cloud (VPC), Virtual Gateway (VGW), and Virtual Private Network (VPN) |
Supported Access Control Policies
- Access control based on the 5-tuple (source IP address, source port, destination IP address, destination port, and protocol)
- Access control based on the domain name
- Access control based on the intrusion prevention system (IPS). The IPS works in observation or interception mode. In block mode, CFW detects and blocks traffic that matches the IPS rules.
- ACL access control policies set for applications, IP address groups, blacklists, and whitelists
Advantages
- Intelligent Defense
CFW has integrated security capabilities and network threat intelligence. Its AI intrusion prevention engine can detect and block malicious traffic in real time. It works with other security services globally to defend against Trojans, worms, injection attacks, vulnerabilities, and phishing attacks.
- High Scalability
CFW can implement refined control on all traffic, including Internet border and cross-VPC traffic, to prevent external intrusions, internal penetration attacks, and unauthorized access from internal to external networks. Its cluster is deployed in HA mode to protect your workloads under heavy traffic.
- Easy-to-Use Application
As a cloud-native firewall, CFW can be enabled easily to import multi-engine security policies with a few clicks, automatically check assets within seconds, and to provide a UI to simplify operations, greatly improving management and defense efficiency.
References
For details about the features and differences between editions, see Features.