HSS is designed to protect server workloads in hybrid clouds and multi-cloud data centers. It provides server security, container security, and web tamper protection (WTP).
HSS can help you remotely check and manage your servers and containers in a unified manner.
HSS protects your system integrity, enhances application security, monitors user operations, and detects intrusions.
Server Security
Host Security Service (HSS) is designed to enhance server security through diverse functions, including asset management, vulnerability detection, baseline checks, intrusion detection, ransomware protection, and web tamper protection (WTP). HSS can comprehensively identify and manage information assets on servers, detect server risks in real time, and prevent intrusions, helping companies build a server security system and reduce threats.
Install the HSS agent on your servers, and you will be able to check the server protection status and risks in a region on the HSS console.
Figure 1 illustrates how HSS works.
Figure 1 Working principles
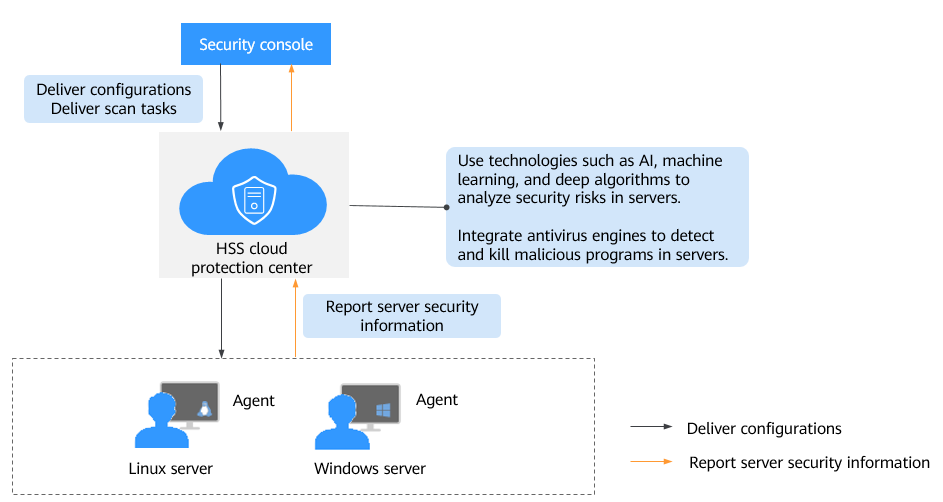
The following table describes the HSS components.
Component | Description |
|---|---|
Management console | A visualized management platform, where you can apply configurations in a centralized manner and view the protection status and scan results of servers in a region. |
HSS cloud protection center |
|
Agent |
|
Container Security
HSS provides container security capabilities. The agent deployed on a server can scan the container images on the server, checking configurations, detecting vulnerabilities, and uncovering runtime issues that cannot be detected by traditional security software. Container security also provides functions such as process whitelist, read-only file protection, and container escape detection to minimize the security risks for a running container.
Web Tamper Protection
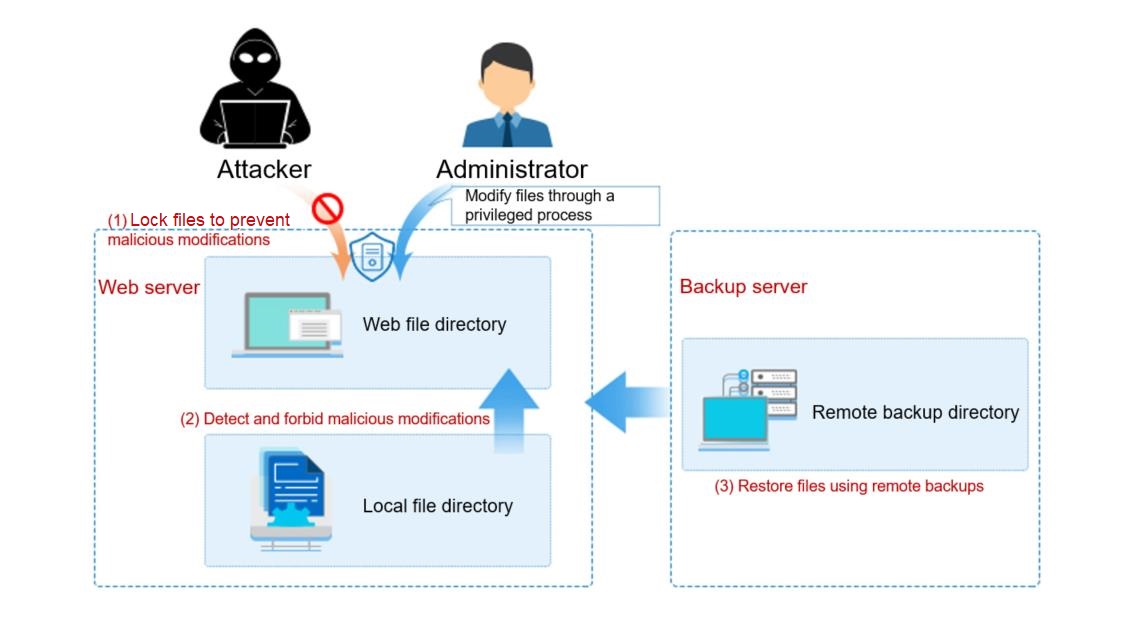
Web Tamper Protection (WTP) monitors website directories in real time and restores tampered files and directories using their backups. It protects website information, such as web pages, electronic documents, and images, from being tampered with or damaged by hackers.
Figure 2 How WTP works