A bucket is a service in cloud computing used for storing and managing data. Data buckets are used to store various types of data files, supporting multiple purposes such as backup, analysis, and content distribution. Static resource buckets are used to host static website content that does not require server-side processing. Setting up OBS buckets helps in efficiently storing and managing data.
Prerequisites
- The OBS bucket to be exported has been created and the endpoint and the OBS bucket name have been obtained.
- After setting up the OBS bucket information, the administrator needs to grant OBS operation permissions synchronously.
Procedure
- Click
 in the upper left corner of the management console to select a region and select an enterprise project from Enterprise Project in the lower left corner of the Workspace page.
in the upper left corner of the management console to select a region and select an enterprise project from Enterprise Project in the lower left corner of the Workspace page. - Click the name of the desired project in the My Projects area in the right pane.
- Click System Settings on the left of the console.
- In the navigation pane on the left, choose Function Settings > OBS Bucket Settings. On the page that appears, set the data bucket parameters.
Figure 1 Data bucket
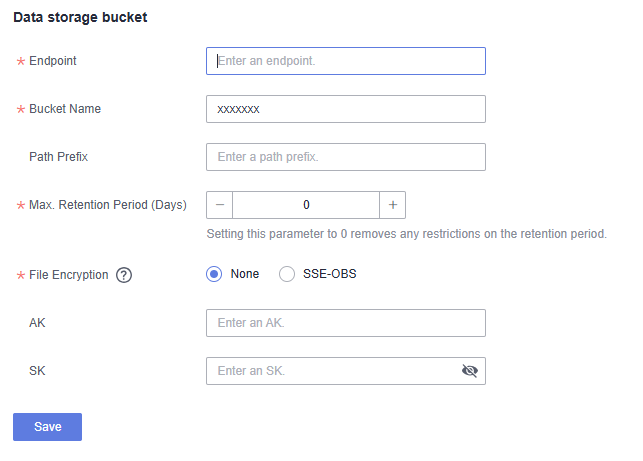
Table 1 Data bucket parameter descriptions Parameter
Description
Endpoint
Endpoint. OBS provides an endpoint for each region. An endpoint can be understood as the regional domain name of OBS in different regions, used to handle access requests for their respective regions.
Bucket Name
A bucket is a container for storing objects in OBS.
Path Prefix
Path where an object is stored in a bucket.
Max. Retention Period (Days)
Retention period, in days.
NOTE:Set this parameter to 0 removes any restrictions on the retention period.
File Encryption
- None: Files to be exported or imported are not encrypted.
- SSE-OBS: Use the SSE-OBS.
AK
Access key ID. It is the unique ID associated with the SK. An AK is used together with an SK to cryptographically sign requests.
SK
Used together with the access key ID to sign requests cryptographically. It identifies a request sender and prevents the request from being modified.
- Set static resource bucket parameters.
- Click Save to complete the configuration.
Figure 2 Static resource bucket
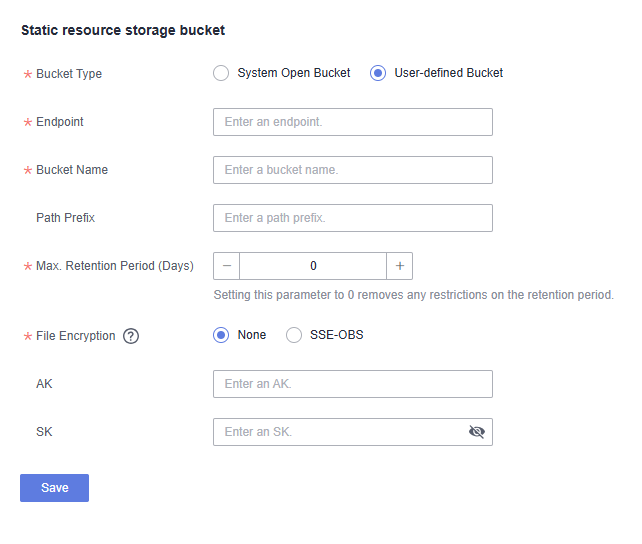
Table 2 Static resource bucket parameter descriptions Parameter
Description
Bucket Type
- System Open Bucket: An OBS public bucket preset by the service, publicly readable and writable by everyone. If it involves private data, use a custom bucket.
- User-defined Bucket: A user-configured OBS bucket that can restrict access permissions with bucket policies to protect private data.
Endpoint
Endpoint. OBS provides an endpoint for each region. An endpoint can be understood as the regional domain name of OBS in different regions, used to handle access requests for their respective regions.
Bucket Name
A bucket is a container for storing objects in OBS.
Path Prefix
Path where an object is stored in a bucket.
Max. Retention Period (Days)
Retention period, in days.
NOTE:Set this parameter to 0 removes any restrictions on the retention period.
File Encryption
- None: Files to be exported or imported are not encrypted.
- SSE-OBS: Use the SSE-OBS.
AK
Access key ID. It is the unique ID associated with the SK. An AK is used together with an SK to cryptographically sign requests.
SK
Used together with the access key ID to sign requests cryptographically. It identifies a request sender and prevents the request from being modified.