Overview
Data Encryption Workshop (DEW) is a comprehensive data encryption service on the cloud. It provides Key Management Service (KMS), Key Pair Service (KPS), and Dedicated Hardware Security Module (Dedicated HSM). DEW uses HSMs to protect the security of your keys, and can be integrated with other services to address data security, key security, and key management issues. You can also use DEW to develop your own encryption applications.
You can use the APIs described in this document to perform operations on keys and key pairs, such as creating, querying, and deleting keys. For details about all supported operations, see API Overview.
API Calling
DEW supports Representational State Transfer (REST) APIs, allowing you to call APIs using HTTPS requests. For details about API calling, see Making an API Request.
Endpoint
An endpoint is the request address for calling an API. Endpoints vary depending on services and regions. For the endpoints of all services, see Regions and Endpoints.
Constraints
For more constraints, see API description.
Concepts
- Region
Regions are divided based on geographical location and network latency. Public services, such as Elastic Cloud Server (ECS), Elastic Volume Service (EVS), Object Storage Service (OBS), Virtual Private Cloud (VPC), Elastic IP (EIP), and Image Management Service (IMS), are shared within the same region. Regions are classified as universal regions and dedicated regions. A universal region provides universal cloud services for common tenants. A dedicated region provides services of the same type only or for specific tenants.
- Availability Zone (AZ)
An AZ comprises one or multiple physical data centers equipped with independent ventilation, fire, water, and electricity facilities. Compute, network, storage, and other resources in an AZ are logically divided into multiple clusters. AZs within a region are interconnected using high-speed optical fibers to support cross-AZ high-availability systems.
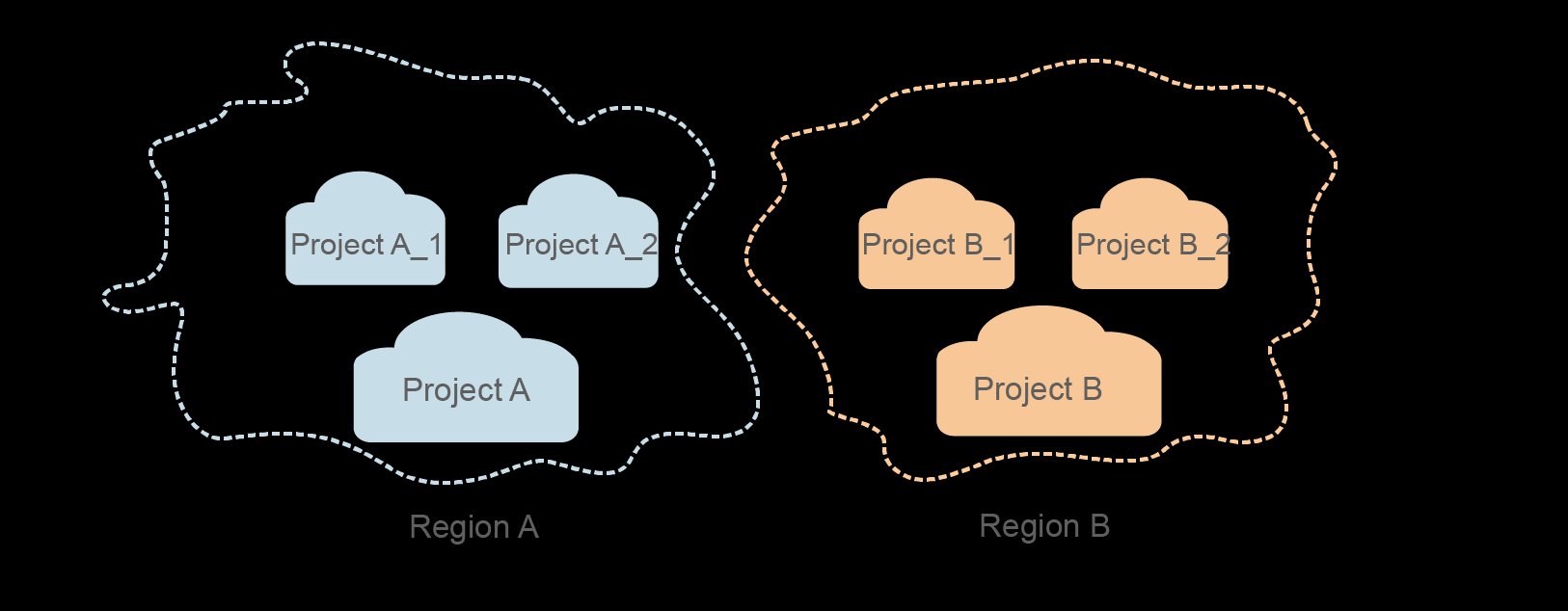
- Project
A project corresponds to a region. Projects group and isolate resources (including compute, storage, and network resources) across physical regions. Users can be granted permissions in a default project to access all resources in the region associated with the project. For more refined access control, create subprojects under a project and create resources in the subprojects. Users can then be assigned permissions to access only specific resources in the subprojects.
Figure 1 Project isolation model